Cybercrime Review: Hackers Cash in on COVID-19
Data Breach Today
SEPTEMBER 22, 2020
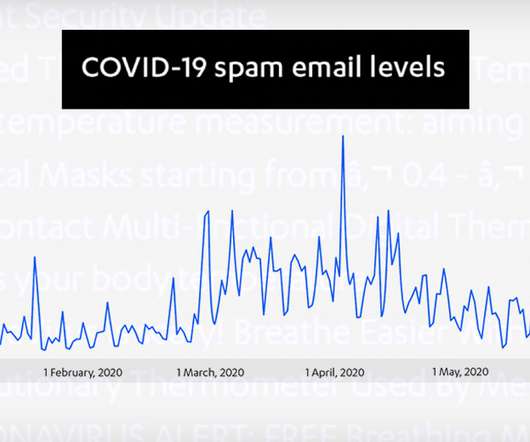
Phishing, Spam, Malware, Social Engineering and Other Recent Attack Trends Reviewing online attack trends for the first half of the year, numerous cybersecurity firms agree: COVID-19 was king. As the pandemic has reshaped how many live and work, so too has it driven attackers to attempt to exploit work-at-home challenges and virus fears.








































Let's personalize your content