Will Europe Force a Facebook Blackout?
WIRED Threat Level
AUGUST 9, 2022
Regulators are close to stopping Meta from sending EU data to the US, bringing a years-long privacy battle to a head.

WIRED Threat Level
AUGUST 9, 2022
Regulators are close to stopping Meta from sending EU data to the US, bringing a years-long privacy battle to a head.

Data Breach Today
AUGUST 9, 2022
Victims Often Attacked Simultaneously by Multiple Ransomware Groups Cybercriminals monitor leak sites for newly listed ransomware victims in a bid to try their own hand at dropping encryption malware, says Sophos. The cybersecurity firm says it's seen an uptick in incidents involving multiple criminal gangs demanding a ransom for unencrypted victims' files.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
AUGUST 9, 2022
Microsoft today released updates to fix a record 141 security vulnerabilities in its Windows operating systems and related software. Once again, Microsoft is patching a zero-day vulnerability in the Microsoft Support Diagnostics Tool (MSDT), a service built into Windows. Redmond also addressed multiple flaws in Exchange Server — including one that was disclosed publicly prior to today — and it is urging organizations that use Exchange for email to update as soon as possible and to en

Data Breach Today
AUGUST 9, 2022
It's not enough for medical device makers to provide a software bill of materials - there also needs to be close attention paid to how vulnerabilities in components are communicated and managed, says medical device security expert Ken Hoyme.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

IT Governance
AUGUST 9, 2022
Welcome to our August 2022 review of phishing attacks, in which we explore the latest email scams and the tactics that cyber criminals use to trick people into handing over their personal data. This month, we look at a scam targeting verified Twitter users and the latest in a series of phishing campaigns that are designed to steal the contents of cryptocurrency wallets.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

eSecurity Planet
AUGUST 9, 2022
Regulatory compliance and data privacy issues have long been an IT security nightmare. And since the EU’s General Data Protection Regulation (GDPR) took effect May 25, 2018, IT compliance issues have been at the forefront of corporate concerns. GDPR, the EU’s flagship data privacy and “right to be forgotten” regulation, has made the stakes of a data breach higher than ever.

Data Breach Today
AUGUST 9, 2022
Feds Say Bitcoin Mercantile Exchange Functioned as a Money Laundering Platform A high-ranking employee at Bitcoin Mercantile Exchange, or BitMEX, has pleaded guilty to violating the Bank Secrecy Act, which requires financial institutions to help prevent money laundering. The plea by Gregory Dwyer follows BitMEX's three founders all pleading guilty to the same charge.
Security Affairs
AUGUST 9, 2022
Cybersecurity researchers from Kaspersky linked the Maui ransomware to the North Korea-backed Andariel APT group. Kaspersky linked with medium confidence the Maui ransomware operation to the North Korea-backed APT group Andariel , which is considered a division of the Lazarus APT Group, . North Korean nation-state actors used Maui ransomware to encrypt servers providing healthcare services, including electronic health records services, diagnostics services, imaging services, and intranet servic

Data Breach Today
AUGUST 9, 2022
The ongoing Russia-Ukraine war has featured cyber operations being used to target Ukraine as well as Russia. But CyberPeace Institute, which tracks cyberattacks tied to the conflict, has so far seen 27 different countries being affected by more than 300 attacks, with many impacting civilians.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Hunton Privacy
AUGUST 9, 2022
On July 27, 2022, Google announced that it is delaying its plans to phase out third-party cookies in the Chrome web browser. Google’s Vice President of Privacy Sandbox, Anthony Chavez, announced the company is extending the full deprecation of third-party cookies to “the second half of 2024,” to continue the testing window for the Privacy Sandbox. Chavez indicated that Google extended the timeline after receiving consistent feedback that developers need more time to evaluate and test the new Pri

KnowBe4
AUGUST 9, 2022
According to the CS Hub Mid-Year Market Report 2022, new findings shows that 75% of survey respondents believe that social engineering and phishing attacks are the top threat vector to cybersecurity within their organization.

Security Affairs
AUGUST 9, 2022
Microsoft Patch Tuesday security updates for August 2022 addressed a zero-day attack remote code execution vulnerability in Windows. Microsoft Patch Tuesday security updates for August 2022 addressed 118 CVEs in multiple products, including.NET Core, Active Directory Domain Services, Azure Batch Node Agent, Azure Real Time Operating System, Azure Site Recovery, Azure Sphere, Microsoft ATA Port Driver, Microsoft Bluetooth Driver, Microsoft Edge (Chromium-based), Microsoft Exchange Server, Microso

Dark Reading
AUGUST 9, 2022
A Q&A with NCC Group's Viktor Gazdag ahead of a Black Hat USA session on CI/CD pipeline risks reveals a scary, and expanding, campaign vector for software supply chain attacks and RCE.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
AUGUST 9, 2022
If you're a Coinbase user, you are most likely the next target of a new phishing campaign. Cybercriminals have managed to infiltrate two-factor authentication and deploying other social engineering strategies with the crypto currency exchange platform.

Hunton Privacy
AUGUST 9, 2022
On July 28, 2022, a federal judge approved TikTok’s $92 million class action settlement of various privacy claims made under state and federal law. The agreement will resolve litigation that began in 2019 and involved claims that TikTok, owned by the Chinese company ByteDance, violated the Illinois Biometric Information Privacy Act (“BIPA”) and the federal Video Privacy Protection Act (“VPPA”) by improperly harvesting users’ personal data.

Hanzo Learning Center
AUGUST 9, 2022
Organizations that use Gmail for business communications need a way to preserve and extract discoverable information in the event of litigation. But that’s harder than it would appear at first glance.
Security Affairs
AUGUST 9, 2022
Cyber Security Specialist Zoziel Pinto Freire shows an example of malicious file analysis presented during his lecture on BSides-Vitória 2022. My objective with this series of articles is to show examples of malicious file analysis that I presented during my lecture on BSides-Vitória 2022. For this first one, I’ll briefly introduce some crucial topics to ease the understanding of the analysis process.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Matters
AUGUST 9, 2022
On Friday, July 8th, the California Privacy Protection Agency (CalPPA) began the formal rulemaking process to adopt proposed regulations to implement California Privacy Rights Act (CPRA) amendments to the California Consumer Privacy Act (CCPA). The initial written comment period will end on August 23, 2022 at 5:00 pm Pacific Time. To cap off the initial comment period, CalPPA will hold a public hearing on August 24th and 25th, during which the agency will accept oral comments and then close th

Dark Reading
AUGUST 9, 2022
The computing giant issued a massive Patch Tuesday update, including a pair of remote execution flaws in the Microsoft Support Diagnostic Tool (MSDT) after attackers used one of the vulnerabilities in a zero-day exploit.

KnowBe4
AUGUST 9, 2022
TradeArabia has published a report about common scams on CashApp, explaining that scammers frequently take advantage of CashApp promotions, like the weekly money giveaway, “Super Cash App Friday.” The scammers will impersonate CashApp and message users over social media, telling them that they’ve won the money. The scammers will then request a transfer fee from the victim.

Threatpost
AUGUST 9, 2022
U.S. Treasury blocked the business of the virtual currency mixer for laundering more than $7 billion for hackers, including $455 million to help fund North Korea’s missile program.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

KnowBe4
AUGUST 9, 2022
Cybercriminals are out there, watching and waiting for the perfect opportunity. They are gathering information about your organization and users, devising the perfect plan to infiltrate your defenses.
Security Affairs
AUGUST 9, 2022
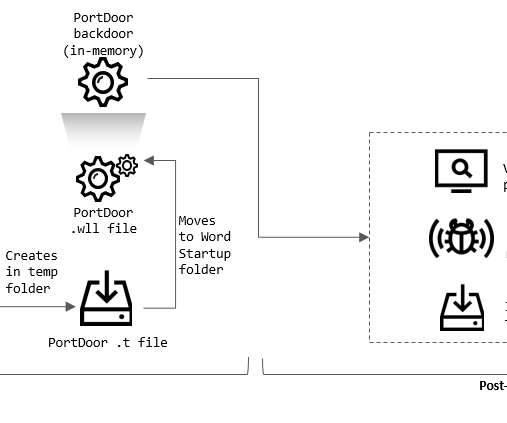
China-linked threat actors targeted dozens of industrial enterprises and public institutions in Afghanistan and Europe. In January 2022, researchers at Kaspersky ICS CERT uncovered a series of targeted attacks on military industrial enterprises and public institutions in Afghanistan and East Europe. The attackers breached dozens of enterprises and in some cases compromised their IT infrastructure, taking over systems used to manage security solutions. “All the victims identified are associ

Dark Reading
AUGUST 9, 2022
The success of Domino's Flex IoT project can be attributed in large part to the security best practices it followed.

Security Affairs
AUGUST 9, 2022
The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned the crypto mixer service Tornado Cash used by North Korea. The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) has sanctioned the crypto mixer service Tornado Cash used by North Korean-linked Lazarus APT Group. Today, Treasury sanctioned virtual currency mixer Tornado Cash, which has been used to launder more than $7 billion worth of virtual currency since its creation in 2019.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
AUGUST 9, 2022
The finding exposes the danger of older, unpatched bugs, which plague at least 4.5 million devices.

WIRED Threat Level
AUGUST 9, 2022
New research found troubling vulnerabilities in the 5G platforms carriers offer to wrangle embedded device data.

Dark Reading
AUGUST 9, 2022
New SOC Analyst Assessment delivers threat-informed training in a live lab environment to help cybersecurity professionals defend their organizations against the latest adversarial tactics and techniques.
Let's personalize your content