Premium Hikes Spur Improved US Cyber Insurance Loss Ratios
Data Breach Today
APRIL 15, 2022
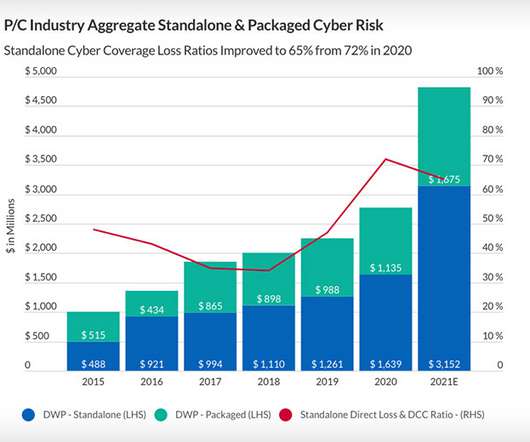
Declining Loss Ratios Means Insurance Premium Increases Might Moderate in Late 2022 A surprising improvement in loss ratios for cyber insurance providers in 2021 means the rapid rise in premiums might at last subside later this year. The loss ratio declined for the first time since 2018 despite the frequency and severity of claims filed for cyberattacks increasing again in 2021.






































Let's personalize your content