What is data governance and why does it matter?
Collibra
FEBRUARY 16, 2022
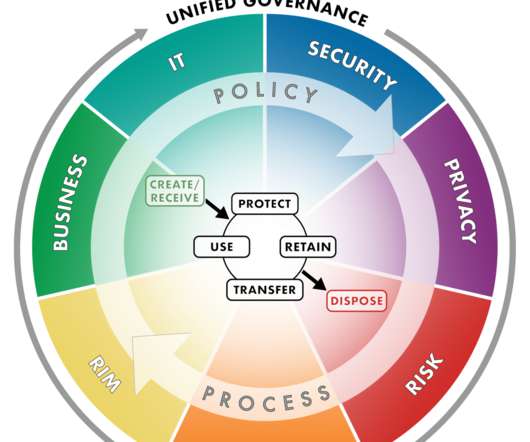
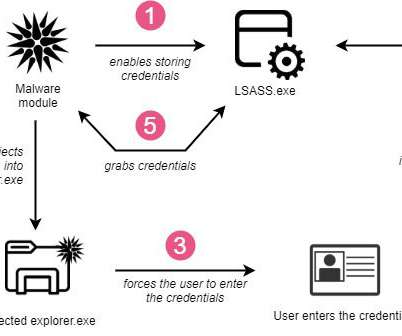
Data governance is the practice of managing and organizing data and processes to enable collaboration and compliant access to data. Data governance allows users to create value from data assets even under constraints for security and privacy. Maybe you shudder when you hear data governance because you imagine people saying “no-” . No , you can’t use the data for that .







































Let's personalize your content