Canadian teenager stole $36 Million in cryptocurrency via SIM Swapping
Security Affairs
NOVEMBER 19, 2021
A Canadian teen has been arrested for his alleged role in the theft of roughly $36.5 million worth of cryptocurrency. A Canadian teenager has been arrested for his alleged role in the theft of roughly $36.5 million worth of cryptocurrency from an American individual. The news of the arrest was disclosed by the Hamilton Police in Ontario, Canada, as a result of a joint investigation conducted by the FBI and the United States Secret Service Electronic Crimes Task Force that started in March 2020.


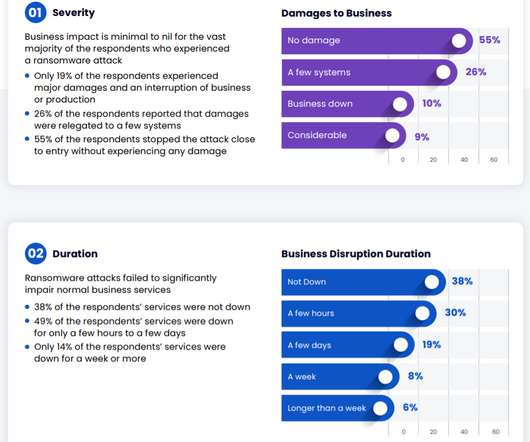

































Let's personalize your content