Accellion: How Attackers Stole Data and Ransomed Companies
Data Breach Today
FEBRUARY 22, 2021
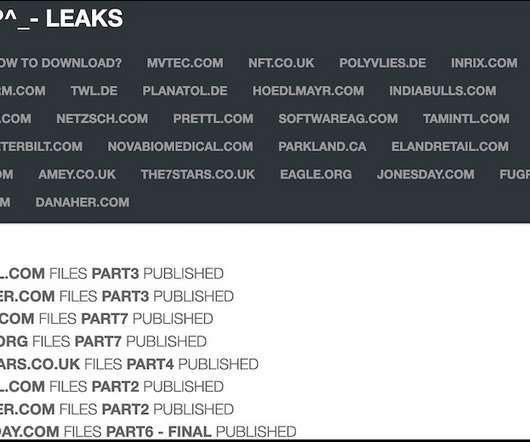
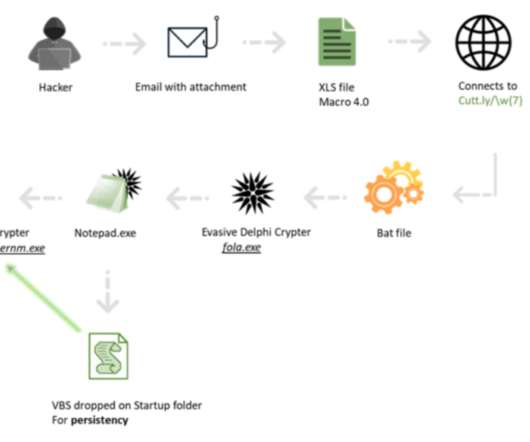
Accellion and Mandiant Say Four Vulnerabilities Have Now Been Patched Software company Accellion has released preliminary findings around the security incident that stung customers using its 20-year-old File Transfer Appliance. The attackers swiftly stole data from compromised systems, and some of those organizations have subsequently been extorted.





































Let's personalize your content