Facebook Delays EU Dating Service Rollout After 'Dawn Raid'
Data Breach Today
FEBRUARY 14, 2020
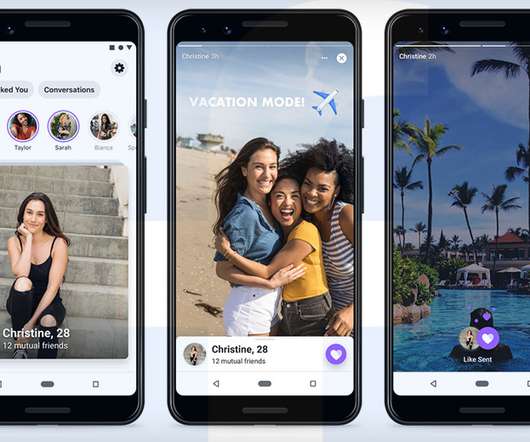
Irish Data Protection Authority Questions Impact of New Service Any lonely hearts in Europe hoping to meet the person of their dreams via Facebook's dating service on Valentine's Day this year will have to wait a little longer. The social network has delayed the EU rollout of its dating service, following a Monday "dawn raid" by Irish privacy investigators.








































Let's personalize your content