Google Observes North Korean APTs Exploiting Chrome
Data Breach Today
MARCH 26, 2022
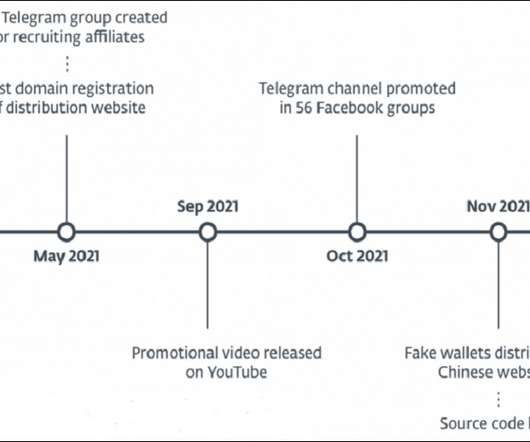
North Korean Hackers Launched Now-Patched Zero-Day Exploit in Two Campaigns Google's threat analysis team has detected a new remote code execution flaw leveraged by North Korean nation-states targeting cryptocurrency, fintech and other industries. Although not named in the report, there appears to be a link to the notorious Lazarus cybercrime group.













Let's personalize your content