Twitter to Charge for Second-Factor Authentication
Data Breach Today
FEBRUARY 20, 2023
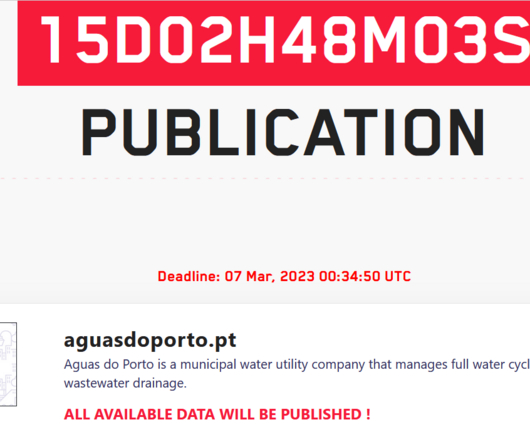
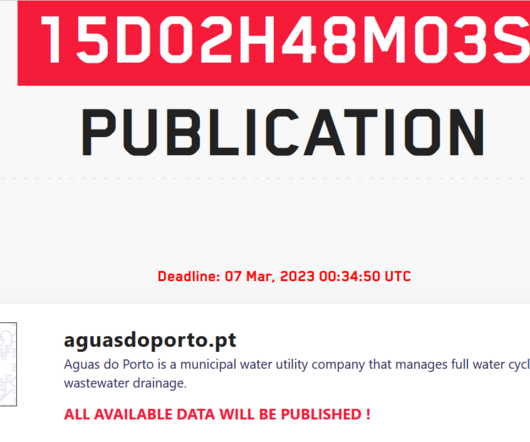
Decision Sparks Concerns That Twitter Accounts Will Be Less Secure Twitter says it will turn off SMS second-factor authentication for all but paying customers starting March 20 in a decision provoking concerns that many customers will be less secure than before. Twitter says 2.6% of active Twitter accounts have activated second-factor authentication.


































Let's personalize your content