FBI: Hackers Targeting US COVID-19 Research Facilities
Data Breach Today
APRIL 17, 2020
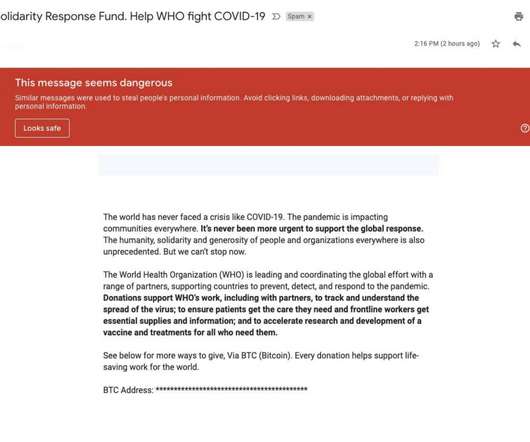
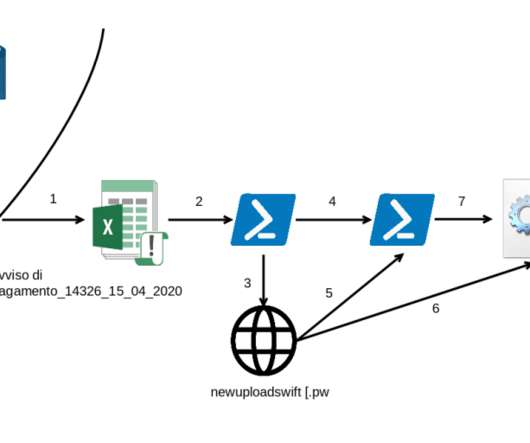
Nation-State Reconnaissance and Intrusion Campaigns Increasing, Expert Says Since the COVID-19 pandemic began earlier the year, the FBI has seen an increase in nation-state hackers targeting U.S. medical research facilities and healthcare organizations conducting research into the virus.







































Let's personalize your content