Enemybot, a new DDoS botnet appears in the threat landscape
Security Affairs
APRIL 17, 2022
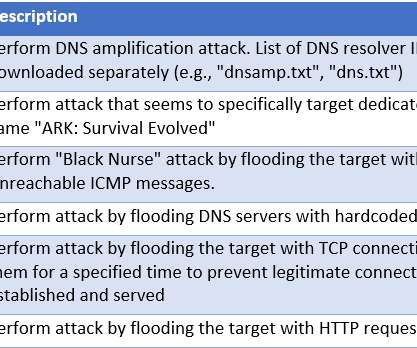
Enemybot is a DDoS botnet that targeted several routers and web servers by exploiting known vulnerabilities. Researchers from Fortinet discovered a new DDoS botnet, tracked as Enemybot, that has targeted several routers and web servers by exploiting known vulnerabilities. The botnet targets multiple architectures, including arm, bsd, x64, and x86. The researchers attribute the botnet to the cybercrime group Keksec which focuses on DDoS-based extortion.












Let's personalize your content