GUEST ESSAY: What everyone can — and should — do to mark Cybersecurity Awareness Month
The Last Watchdog
OCTOBER 18, 2021
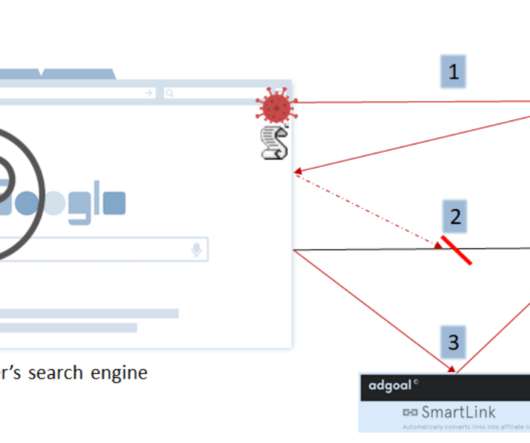
With new technological advancements comes a need for heightened security measures. Plenty of criminals are searching for vulnerabilities in networks, so it shouldn’t come as a surprise that cybersecurity issues have become more prevalent. Related: President Biden issues cybersecurity executive order. For the past 17 years, October has been designated as National Cybersecurity Awareness Month (NCSAM) to focus much needed attention on cybersecurity.






































Let's personalize your content