The latest variant of the new Ginp Android Trojan borrows code from Anubis
Security Affairs
NOVEMBER 30, 2019
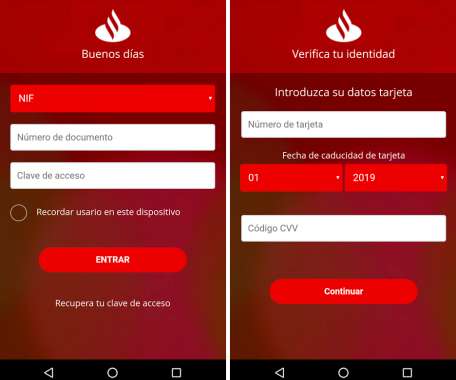
Security experts discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Security experts at ThreatFabric discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Ginp was first spotted in October by Kaspersky while targeting Spain and UK, but researchers believe it has been active around since June.












Let's personalize your content