UK's Brexit Transition Period: Keep Complying With GDPR
Data Breach Today
FEBRUARY 7, 2020
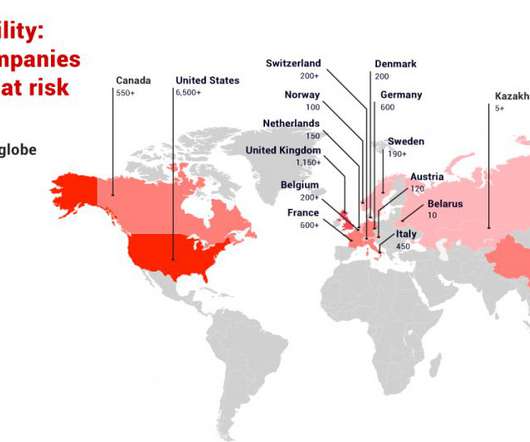
Privacy Rules Remain in Effect Pending Eventual Outcome of UK-EU Negotiations As former U.K. Prime Minister Theresa May famously declared: "Brexit means Brexit." But what Britain's exit from the EU means for the nation's data privacy rules and future EU-U.K. data flows remains to be seen, as the country navigates its post-Brexit transition period.





































Let's personalize your content