6 Unique InfoSec Metrics CISOs Should Track in 2020
Dark Reading
JANUARY 10, 2020
You might not find these measurements on a standard cybersecurity department checklist. But they can help evaluate risks you haven't even considered yet.

Dark Reading
JANUARY 10, 2020
You might not find these measurements on a standard cybersecurity department checklist. But they can help evaluate risks you haven't even considered yet.

Information Management Resources
JANUARY 10, 2020
Companies are moving away from the traditional waterfall approach and adopting commercial software best practices such as the Agile and DevOps methodologies that are lean, iterative and incremental.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JANUARY 10, 2020
But Electric Sector, Driven by Regulators, Has Been Adapting, Experts Say Hackers have been increasingly probing the North American power grid for weaknesses, but the industry - driven in part by regulators - is increasingly able to identify and repel attackers, industrial cybersecurity experts say.
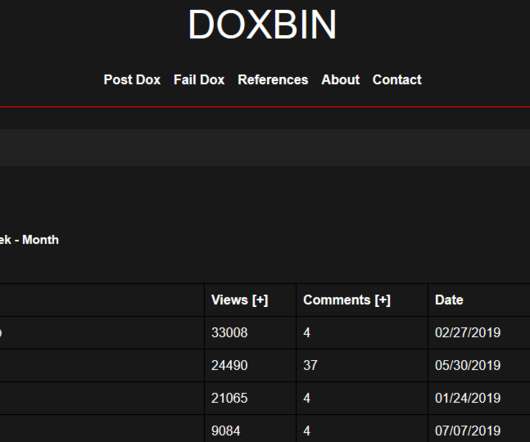
Krebs on Security
JANUARY 10, 2020
Federal investigators on Friday arrested a Virginia man accused of being part of a neo-Nazi group that targeted hundreds of people in “swatting” attacks, wherein fake bomb threats, hostage situations and other violent scenarios were phoned in to police as part of a scheme to trick them into visiting potentially deadly force on a target’s address.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
JANUARY 10, 2020
Congress Wants Security Vulnerabilities Addressed to Thwart Foreign Interference The CEOs of the three largest voting machine manufacturers testified before a U.S. Congressional committee that they would be open to greater federal oversight of their equipment to help ensure the security of voting data in upcoming elections, including the 2020 presidential contest.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
JANUARY 10, 2020
Federal Judge Still Considering Objections From Privacy Groups Six months after Facebook agreed to a landmark privacy settlement with the U.S. Federal Trade Commission that resulted in a $5 billion fine, a federal judge is still considering objections from advocacy groups that claim the deal doesn't go far enough.

WIRED Threat Level
JANUARY 10, 2020
A bad code update allowed anyone to easily reveal which accounts posted to Facebook Pages—including celebrities and politicians—for several hours. .

Data Breach Today
JANUARY 10, 2020
Prosecutors: Defendant Reported Hospital Worker for HIPAA Crimes That Never Happened In a bizarre "whistleblower" case, federal prosecutors have charged a Georgia man in connection with an alleged "intricate scheme" involving falsely reporting that a Savannah hospital worker committed criminal HIPAA violations.
OpenText Information Management
JANUARY 10, 2020
At this year’s Forrester Data Strategy & Insights conference in Austin, TX, Forrester’s Boris Evelson presented a live technology challenge to OpenText and another vendor in his session, “Best in Class Platforms.” The challenge was to ingest a data set of more than 150,000 wine reviews live on stage and demonstrate which insights OpenText™ Magellan™ … The post Unlocking insights trapped in unstructured wine reviews appeared first on OpenText Blogs.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
JANUARY 10, 2020
Retailer's Missteps Led to 'Careless Loss of Data,' Privacy Watchdog Says British regulators have fined Dixons Carphone $653,000 for a breach that exposed millions of payment card details and personal data due to point-of-sale malware. The retailer's lack of security contributed to a "careless loss of data," says the Information Commissioner's Office.

WIRED Threat Level
JANUARY 10, 2020
Mark Zuckerberg promised default end-to-end encryption throughout Facebook's platforms. Nearly a year later, Messenger's not even close.

Data Breach Today
JANUARY 10, 2020
The latest edition of the ISMG Security Report discusses "Orwellian" surveillance activity in 2020 via the ToTok app. Also featured: the controversy over enabling law enforcement to circumvent encryption; the cyberattack risks posed by IoT devices.

IT Governance
JANUARY 10, 2020
Dixons Carphone is facing a £500,000 fine from the ICO (Information Commissioner’s Office), following a cyber attack that affected millions of customers. An investigation by the UK’s data protection watchdog found cyber criminals had compromised the retailer’s payment systems and siphoned off the credit and debit card information of 14 million customers.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Data Breach Today
JANUARY 10, 2020
The latest edition of the ISMG Security Report discusses "Orwellian" surveillance activity in 2020 via the ToTok app. Also featured: the controversy over enabling law enforcement to circumvent encryption; the cyberattack risks posed by IoT devices.

Security Affairs
JANUARY 10, 2020
The US DHS CISA agency is warning organizations that threat actors continue to exploit the CVE-2019-11510 Pulse Secure VPN vulnerability. The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) is warning organizations that attackers continue to exploit the well known Pulse Secure VPN vulnerability tracked as CVE-2019-11510.

Data Breach Today
JANUARY 10, 2020
Is it possible that a nation-state actor such as Iran could create a cybersecurity incident that compromises the U.S. power grid? Bernie Cowens, most recently CISO at the nation's largest electric utility, says that's unlikely because the power grid is more cybersecure than you might think.

OpenText Information Management
JANUARY 10, 2020
Everyone who has taken a long road trip with children has heard that incessant question from the back seat: “Are we there yet?” In a customer journey that same question is often asked, but buyers and sellers have different agendas and ideas about what getting “there” means. The sellers know their target destination – purchase … The post Are we there yet?

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Breach Today
JANUARY 10, 2020
Researchers are attempting to develop new forms of cryptography that could not be cracked by powerful quantum computing devices that are in the works. Divesh Aggarwal, principal investigator at Singapore's Center for Quantum Technologies, describes the efforts.
Security Affairs
JANUARY 10, 2020
Officials at the Albany County Airport Authority revealed that New York airport servers were infected with ransomware on Christmas. Officials at the Albany County Airport Authority announced this week that a ransomware attack hit the New York airport and its computer management provider LogicalNet over Christmas. The news of the attack was disclosed after LogicalNet reported its own management services network had been breached.

Data Matters
JANUARY 10, 2020
The California Department of Business Oversight (CDBO) recently concluded that the point of sale consumer financing programs offered by Sezzle, Inc., and another, unnamed party constituted making loans for purposes of the California Financing Law (CFL). A number of payment providers and technology companies have been developing innovative payment options, including consumer financing options, that are facilitated by advances in technology and mobile connectivity.
Security Affairs
JANUARY 10, 2020
A flaw, dubbed Cable Haunt, in Broadcom’s cable modem firmware exposed as many as 200 million home broadband gateways in Europe alone, at risk of remote hijackings. Hundreds of millions of Broadcom-based cable modems are at risk of remote hijacking due to the presence of a vulnerability dubbed Cable Haunt, CVE-2019-19494. The flaw resides in the hardware and software component of Broadcom chips called a spectrum analyzer that protects the cable modem from signal surges and disturbances com

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

OpenText Information Management
JANUARY 10, 2020
Have you ever headed out to your car on a cold, winter morning only to find the windshield completely frosted with ice? If you’re in a hurry, you may not scrape all the frost off the windshield or wait long enough for the car’s defroster to fully perform the job. Visibility is limited to the … The post 7 must-have features for end-to-end data visibility appeared first on OpenText Blogs.
Security Affairs
JANUARY 10, 2020
Two MageCart groups have planted software skimmers on multiple European websites for the Perricone MD anti-aging skincare. Two distinct MageCart groups have compromised multiple European websites for the Perricone MD anti-aging skin-care brand with the intent of stealing customer payment card info. The two groups planted software skimmers on Perricone MD websites in Italy , Germany , and the U.K. , fortunately, at the time no credit card data seem to have been stolen. “During research int

OpenText Information Management
JANUARY 10, 2020
Health and safety regulations are among the toughest in force worldwide, but in 2018 there were 2.8 million workplace injuries in the U.S. alone that amounted to nearly $60 billion in direct U.S. workers compensation costs. That equates to $1 billion that US businesses are paying in serious injuries every week. Smart Personal Protection Equipment (PPE) … The post The role of smart Personal Protection Equipment appeared first on OpenText Blogs.
Troy Hunt
JANUARY 10, 2020
I really should have started the video about 3 minutes earlier. Had I done that, you'd have caught me toppling backwards into the frangipani tree whilst trying to position my chair and camera which frankly, would have made for entertaining viewing. Instead, this week's update is focused primarily on a completely different epic fail, namely Surebet247's handling of a breach impacting their customers.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Threatpost
JANUARY 10, 2020
Researchers say that physically disruptive attacks aren't imminent, but an increased focus on U.S. electrical-grid operators doesn't bode well.
Everteam
JANUARY 10, 2020
This week, Everteam hosted a webinar called Conducting an Information Assets Inventory. In this session, we covered the what, how, and why of an information asset inventory process. Below are some key takeaways from the discussion. Information assets hide everywhere, dispersed throughout the enterprise – undiscovered and untapped – and data production is growing exponentially.

Dark Reading
JANUARY 10, 2020
The approach allowed researchers to use machine learning on encrypted data without first decrypting it.
Let's personalize your content