 Under the guise of determining applicant eligibility for a U.S. federal government job, this latest phishing attack plants the seed for a future attack on the victim organization.
Under the guise of determining applicant eligibility for a U.S. federal government job, this latest phishing attack plants the seed for a future attack on the victim organization.
We’ve covered plenty of cyberattacks here that leverage a leaked version of Cobalt Strike Beacon to execute PowerShell scripts, log keystrokes, take screenshots, download files, and spawn other payloads. But normally, the use of Cobalt Strike Beacon has been covered in conjunction with a completed (and successful) attack on an organization.
But security researchers at Cisco Talos have identified an attack where the goal is simply to deliver Cobalt Strike Beacon – likely to be used by another threat actor who has purchased the access on the Dark Web. Targeting U.S. and New Zealand victims, the campaigns pose as government agencies or trade unions offering the victim assistance in obtaining a job.
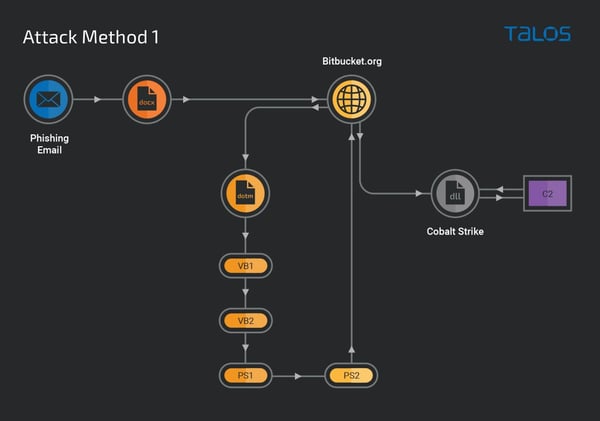
In one variant of the attack, the malicious Word documents pull a first stage VB dropper from bitbucket[.]com which decodes part of its contents to a second VB dropper, which – in turn – decodes its contents to PowerShell script (this happens twice, similar to the VB droppers), when – finally – the Cobalt Strike Beacon is downloaded from bitbucket.
Source: Cisco Talos
The obfuscation and evasion techniques used in the form of repeatedly encoding content and using two different scripting languages demonstrates the lengths attackers will go to in order to avoid detection. And the Beacon payload makes this attack even more dangerous – as the victim organizations are now susceptible to further attack.
The infection point in this attack lies with the victim user, who is most definitely not thinking about whether the assistance email (and its’ Word doc attachment) are malicious in nature or not. But with proper Security Awareness Training, users can be taught to see through documents that “require” macros be turned on, etc. for what they really are: the beginnings of a cyber attack.
 Here's how it works:
Here's how it works:




