Hackers Post Details on MGM Resorts Guests: Report
Data Breach Today
FEBRUARY 20, 2020
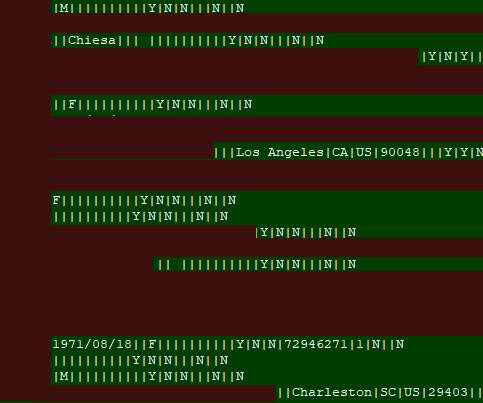
Breached Cloud Server Contained Data on 10 Million Guests Hackers have posted on an underground forum the personal information of 10.6 million MGM Resorts guests, ZDNet reports. The hotel chain confirms it was breached last year.










































Let's personalize your content