The latest variant of the RapperBot botnet adds cryptojacking capabilities
Security Affairs
MAY 14, 2023
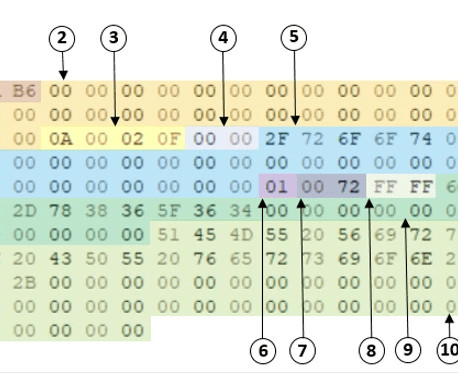
FortiGuard Labs Researchers spotted new samples of the RapperBot botnet that support cryptojacking capabilities. FortiGuard Labs researchers have discovered new samples of the RapperBot bot that added cryptojacking capabilities. Researchers from FortiGuard Labs first discovered the previously undetected RapperBot IoT botnet in August, and reported that it is active since mid-June 2022.













Let's personalize your content