Exclusive: Resecurity discovered 0-day vulnerability in TP-Link Wi-Fi 6 devices
Security Affairs
NOVEMBER 26, 2021
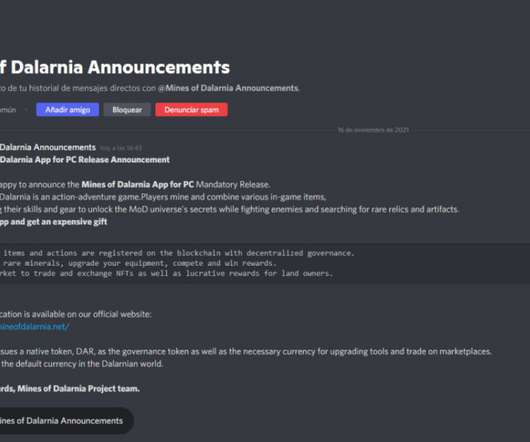
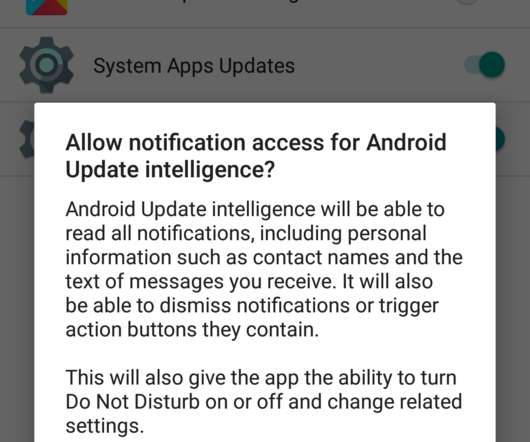
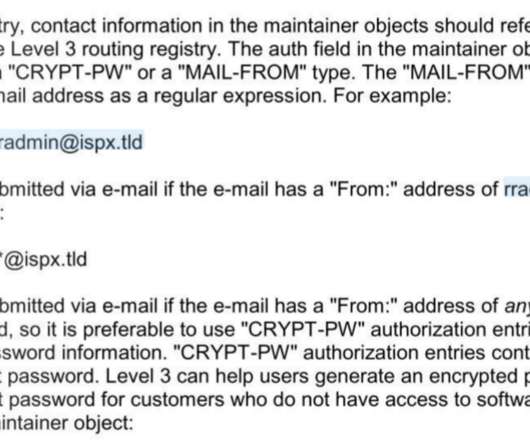
Resecurity researchers found a zero-day vulnerability in the TP-Link enterprise device with model number TL-XVR1800L. Resecurity, a Los Angeles-based cybersecurity company has identified an active a zero-day vulnerability in the TP-Link device with model number TL-XVR1800L (Enterprise AX1800 Dual Band Gigabit Wi-Fi 6 Wireless VPN Router), which is primarily suited to enterprises.


















Let's personalize your content