Emotet Malware Automatically Uninstalled
Data Breach Today
APRIL 26, 2021
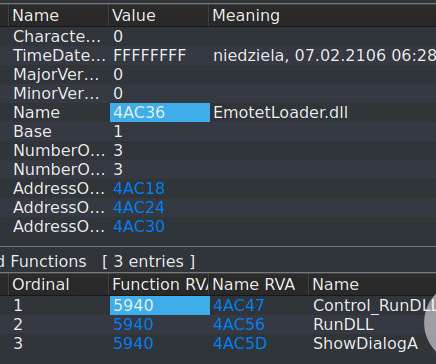
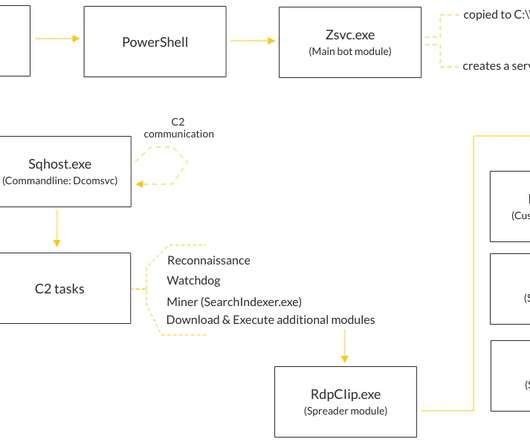
Law Enforcement 'Update' to Erase Malware From Infected Devices Activated An "update" pushed out earlier this year by law enforcement agencies, including Europol, on Sunday began erasing Emotet malware from infected devices worldwide, Malwarebytes reports. The move comes after the FBI recently remotely removed web shells from vulnerable on-premises Microsoft Exchange servers.






































Let's personalize your content