Fueled by Profits, Ransomware Persists in New Year
Data Breach Today
JANUARY 21, 2021
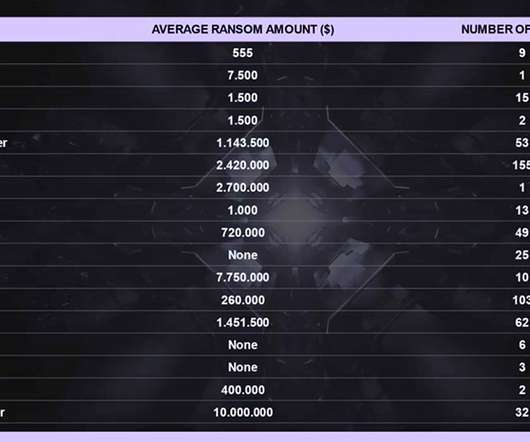
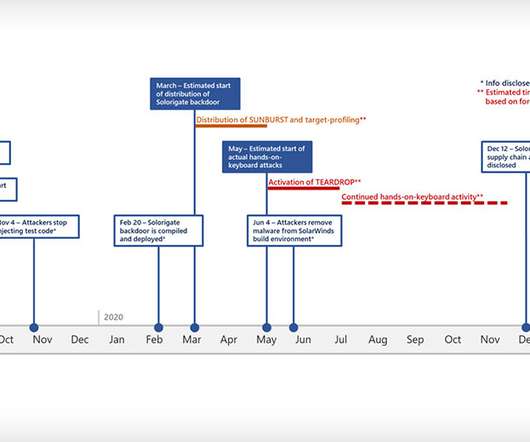
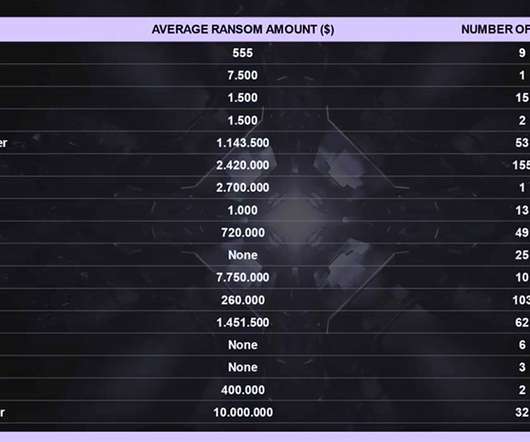
Increasing Ransomware Varieties and Attack Volume Look Set to Continue, Experts Warn Ransomware dominated the cybercrime landscape in 2020 and looks set to do so again this year, as criminals seek fresh new ways to make victims pay. Experts predict gangs will double down on whatever works, which lately includes data exfiltration.





































Let's personalize your content