Prometei botnet evolves and infected +10,000 systems since November 2022
Security Affairs
MARCH 11, 2023
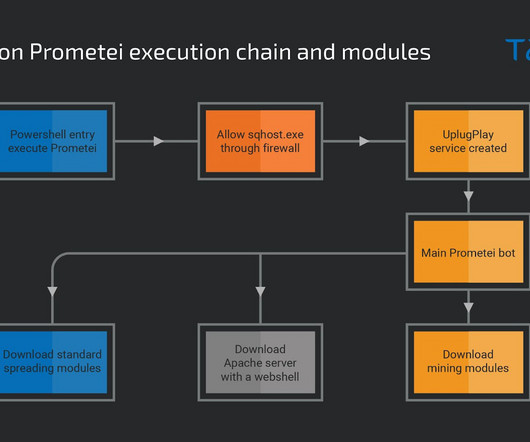
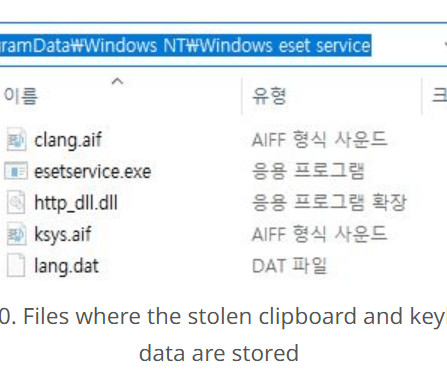
A new version of the Prometei botnet has infected more than 10,000 systems worldwide since November 2022, experts warn. Cisco Talos researchers reported that the Prometei botnet has infected more than 10,000 systems worldwide since November 2022. The crypto-mining botnet has a modular structure and employs multiple techniques to infect systems and evade detection.












Let's personalize your content