Thousands Zoom credentials available on a Dark Web forum
Security Affairs
APRIL 12, 2020
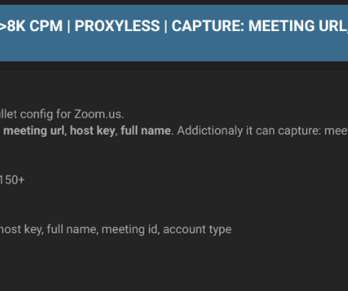
Security researchers discovered an archive available on a dark web forum that includes thousands of compromised Zoom credentials. Researchers discovered a database available on an underground forum in the dark web that contained more than 2,300 compromised Zoom credentials. Some of the records also included meeting IDs, names and host keys. The archive included credentials for Zoom accounts belonging to organizations in various industries, including banking, consultancy, healthcare software comp














Let's personalize your content