The Future of Ransomware
Dark Reading
DECEMBER 21, 2021
Focusing on basic security controls and executing them well is the best way to harden your systems against an attack.

Dark Reading
DECEMBER 21, 2021
Focusing on basic security controls and executing them well is the best way to harden your systems against an attack.

The Last Watchdog
DECEMBER 21, 2021
Cloud hosted email services have come into wide use as the go-to communication and collaboration work tools for businesses far and wide. Related: Weaponized email endures as top threat. Digital native companies start from day one relying entirely on Microsoft Office 365 or Google’s G Suite and most established companies are in some stage of migrating to, or adjusting for, Office 365 or G Suite.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 21, 2021
Microsoft warns of a couple of Active Directory flaws fixed with the November 2021 Patch Tuesday updates that could allow takeover of Windows domains. Microsoft released an alert on a couple of Active Directory vulnerabilities, that have been fixed with the November 2021 Patch Tuesday security updates, that could allow threat actors to takeover Windows domains.

eSecurity Planet
DECEMBER 21, 2021
There are few guarantees in the IT industry, but one certainty is that as the world steps into 2022, ransomware will continue to be a primary cyberthreat. The dangers from ransomware have risen sharply since WannaCry and NotPetya hit the scene in 2017, and this year has been no different. A pair of recent reports underscores just how big that threat is.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
DECEMBER 21, 2021
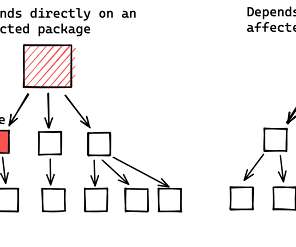
Google found more than 35,000 Java packages in the Maven Central repository that are impacted by flaws in the Apache Log4j library. The Google Open Source Team scanned the Maven Central Java package repository and found that 35,863 packages (8% of the total) were using versions of the Apache Log4j library vulnerable to Log4Shell exploit and to the CVE-2021-45046 RCE. “More than 35,000 Java packages, amounting to over 8% of the Maven Central repository (the most significant Java package
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
DECEMBER 21, 2021
Two new directors elected by members of the association. The Association for Intelligent Information Management ( AIIM ), announces the election of two new board members following its Annual Meeting held in early December. The following directors will serve on the AIIM Board of Directors beginning January 1, 2022 through December 31, 2024: Jason Cassidy, Shinydocs.
Security Affairs
DECEMBER 21, 2021
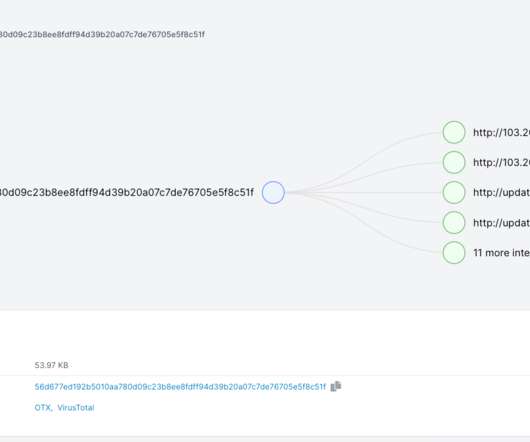
Researchers spotted a new botnet named Abcbot hat that mainly targeted Chinese cloud hosting providers over the past months. Security researchers discovered a new botnet, named Abcbot , that focused on Chinese cloud hosting providers over the past months. The list of targeted providers includes Alibaba Cloud, Baidu, Tencent, and Huawei Cloud. In November, researchers from Qihoo 360’s Netlab security team spotted the Abcbot botnet that was targeting Linux systems to launch distributed denial-of-s

Threatpost
DECEMBER 21, 2021
Microsoft is urging customers to patch two Active Directory domain controller bugs after a PoC tool was publicly released on Dec. 12.

Dark Reading
DECEMBER 21, 2021
The Facebook parent company seeks court's help in identifying the individuals behind some 39,000 websites impersonating its brands to collect login credentials.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Threatpost
DECEMBER 21, 2021
APT attackers are using a security vulnerability in ManageEngine Desktop Central to take over servers, deliver malware and establish network persistence.

Security Affairs
DECEMBER 21, 2021
A Russian national was extradited to the US from Switzerland after he was charged for trading information stolen from hacked U.S. companies. The Russian national Vladislav Klyushin (41) was extradited to the United States from Switzerland to face charges for his alleged role in a scheme whose participants traded on information stolen from U.S. companies.

Dark Reading
DECEMBER 21, 2021
If security teams are not logging everything, they are increasing security risk and making it more difficult to investigate and recover from a data breach. Modern log management goes beyond just a SIEM.

Jamf
DECEMBER 21, 2021
Shared iOS or iPadOS devices in the workplace can lead to password fatigue, as employees are forced to log in to multiple apps per shift. With Single Login for Jamf Setup and Jamf Reset, you can streamline workflows and allow your IT admins to be heroes.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
DECEMBER 21, 2021
For zero trust to be successful, organizations need to be able to check user identity, device posture, and overall behavior without adding friction to the experience.

Threatpost
DECEMBER 21, 2021
A quarter-billion of those passwords were not seen in previous breaches that have been added to Have I Been Pwned.

IG Guru
DECEMBER 21, 2021
December 20, 2021 – DALLAS – The Association of Certified E-Discovery Specialists (ACEDS), the world’s leading organization for training and certification in e-discovery and part of The BARBRI Group, announces today a new affinity partnership with IG GURU, a news and community site for Information Governance professionals. IG GURU’s mission to provide industry news and host a […].

Threatpost
DECEMBER 21, 2021
Yaron Kassner, CTO and co-founder of Silverfort, discusses why using all-seeing privileged accounts for monitoring is bad practice.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
DECEMBER 21, 2021
Data from dozens of penetration tests and security assessments suggest nearly every organization can be infiltrated by cyberattackers.

Security Affairs
DECEMBER 21, 2021
Uptycs researchers have observed attacks related to miners, DDOS malware and some variants of ransomware actively leveraging LogforShell flaw in log4j. Last week the Log4j vulnerability turned the internet upside down. The impact of the vulnerability is massive and attackers have started taking advantage of the flaw. So far we have observed attacks related to coinminers, DDOS malware and some variants of ransomware actively leveraging this vulnerability.

Dark Reading
DECEMBER 21, 2021
Zero trust is key to not falling victim to the next big vulnerability.

Threatpost
DECEMBER 21, 2021
There are 17,000npatched Log4j packages in the Maven Central ecosystem, leaving massive supply-chain risk on the table from Log4Shell exploits.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

DXC Technology
DECEMBER 21, 2021
????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????? ???????????????????????????????????????????????????????????????????????????????????????????????????? ??????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????

Jamf
DECEMBER 21, 2021
To help you figure out the best practices for your organization, our webinar, How to Manage FileVault with Jamf , offers expert guidance on how to access the full potential of remote management of FileVault.

Hanzo Learning Center
DECEMBER 21, 2021
In the wake of the ongoing social justice crisis in the United States, Hanzo—like many companies—has been reevaluating its policies and practices around diversity, equity, and inclusion. With the end-of-year holiday season upon us, we’ve been wondering: how can we create a culture that’s inclusive and welcoming to all? How can those of us who celebrate Christmas keep our hearts and minds open to those of us who don’t—or to those for whom the season just isn’t worth celebrating?

Dark Reading
DECEMBER 21, 2021
The UK's NCA and NCCU have shared 225 million stolen emails and passwords with HIBP, which tracks stolen credentials.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Reltio
DECEMBER 21, 2021
Reltio Founder and CTO, Manish Sood, recently attended the AWS re:Invent 2021 conference in Las Vegas where he spent time with editors of TheCUBE.net. The following includes key takeaways from that discussion, including a history of the company and what the future holds. You can watch the segment here: [link]. Reltio’s Origins. Manish has spent much of his career trying to solve a problem that most large companies have – getting all their applications on the same page to generate reliable and tr
Let's personalize your content