How to Navigate the Mitigation of Deepfakes
Dark Reading
NOVEMBER 17, 2021
Deepfakes are already several steps ahead of the technology that can detect and warn us about them.

Dark Reading
NOVEMBER 17, 2021
Deepfakes are already several steps ahead of the technology that can detect and warn us about them.
Security Affairs
NOVEMBER 17, 2021
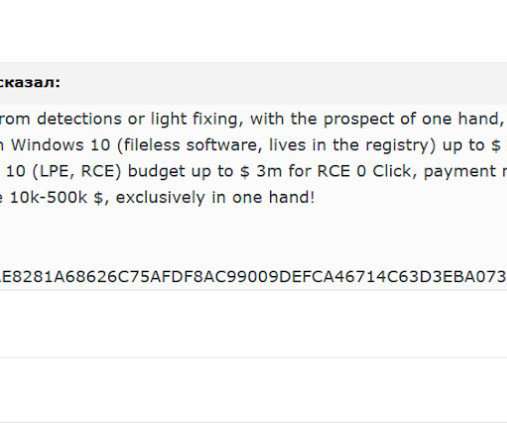
Researchers detailed the multi-millionaire market of zero-day exploits, a parallel economy that is fueling the threat landscape. Zero-day exploits are essential weapons in the arsenal of nation-state actors and cybercrime groups. The increased demand for exploits is fueling a millionaire market where these malicious codes are incredibly expensive. Researchers from Digital Shadows published an interesting research titled “ Vulnerability Intelligence: Do you know where your flaws are?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
NOVEMBER 17, 2021
I received email from two people who told me that Microsoft Edge enabled synching without warning or consent, which means that Microsoft sucked up all of their bookmarks. Of course they can turn synching off, but it’s too late. Has this happened to anyone else, or was this user error of some sort? If this is real, can some reporter write about it?

Dark Reading
NOVEMBER 17, 2021
Machine learning delivers plenty of benefits. But as the emerging technology gets applied more broadly, be careful about how you handle all the data used in the process.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

DLA Piper Privacy Matters
NOVEMBER 17, 2021
On 16 November 2021, the English High Court declined to strike-out a claim for damages for distress following an isolated one-off data incident which was quickly remedied. In doing so, however, the Court: confirmed that the de minimis concept is equally applicable to claims under the GDPR and Data Protection Act 2018, as it was to claims under the Data Protection Act 1998; held that a claim for injunctive and declaratory relief in circumstances such as those present in this case was misconceived
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Threatpost
NOVEMBER 17, 2021
Threat actors used malicious emails to target more than 125 people with high-profile TikTok accounts in an attempt to steal info and lock them out.

Jamf
NOVEMBER 17, 2021
Jamf’s sponsorship of the Acronis #CyberFit Summit in Miami provided the occasion to reflect on our integration with Acronis Cyber Protect Cloud, which allows Managed Service Proviers (MSPs) to remotely deploy Acronis’s backup, recovery, security and endpoint protection using native Jamf tools and workflows.

Security Affairs
NOVEMBER 17, 2021
Netgear addressed a code execution vulnerability, tracked as CVE-2021-34991, in its small office/home office (SOHO) devices. Netgear addressed a pre-authentication buffer overflow issue in its small office/home office (SOHO) devices that can be exploited by an attacker on the local area network (LAN) to execute code remotely with root privileges. The flaw, tracked as CVE-2021-34991 (CVSS score of 8.8), resides in the device’s Universal Plug-and-Play (UPnP) upnpd daemon functions related to the

Thales Cloud Protection & Licensing
NOVEMBER 17, 2021
DHS And NIST Release Guidance for The Adoption of Post-Quantum Cryptography. divya. Thu, 11/18/2021 - 06:28. The Department of Homeland Security (DHS), in partnership with the National Institute of Standards and Technology (NIST), has released a roadmap to help organizations protect their data and systems and to reduce risks related to the advancement of quantum computing technology.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Threatpost
NOVEMBER 17, 2021
Meanwhile, a Microsoft analysis that followed six Iranian threat actor groups for over a year found them increasingly sophisticated, adapting and thriving.
Security Affairs
NOVEMBER 17, 2021
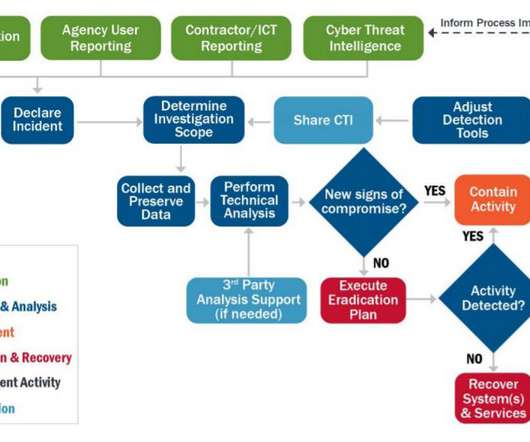
CISA released the Federal Government Cybersecurity Incident Response Playbooks for the federal civilian executive branch agencies. The Cybersecurity and Infrastructure Security Agency (CISA) has released new cybersecurity response plans for federal civilian executive branch (FCEB) agencies (” Federal Government Cybersecurity Incident and Vulnerability Response Playbooks “).

Threatpost
NOVEMBER 17, 2021
WordPress sites have been splashed with ransomware warnings that are as real as dime-store cobwebs made out of spun polyester.

IG Guru
NOVEMBER 17, 2021
Jensen Beach, FL. – The worldwide pandemic has brought increased attention to privacy, CSR Privacy Solutions (CSR), a privacy compliance company headquartered in Jensen Beach, Florida, has hired new staff to accommodate growth Jennie Gift. Jennie, a former vice president at both Shred Nations/Record Nations and Paxton Records. Jennie is based out of Denver, Colorado and bears responsibility for […].

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Protection Report
NOVEMBER 17, 2021
Bill 64, which purports to modernise Québec’s privacy legislation, was recently passed. This sweeping reform of the province’s framework for processing personal information hinges on three main axes: increased obligations for enterprises that collect or otherwise process personal information, the creation of new rights for persons whose information is collected, and. the imposition of far more stringent sanctions for failing to comply with the law.

Threatpost
NOVEMBER 17, 2021
Lures dressed up to look like movie and TV streaming offers are swiping payment data.
WIRED Threat Level
NOVEMBER 17, 2021
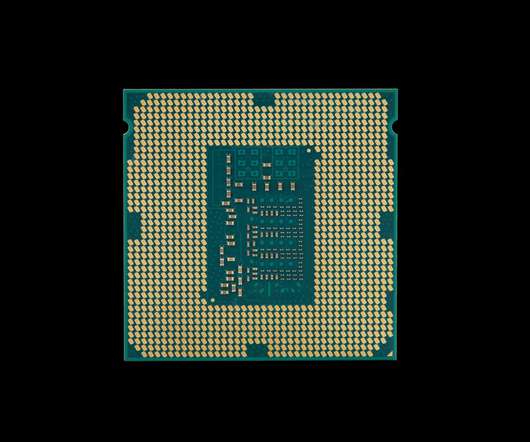
The vulnerability allows an attacker with physical access to the CPU to bypass the security measures protecting some of its most sensitive data.

Data Protection Report
NOVEMBER 17, 2021
On November 8, 2021, New York became the third state to require private employers to provide employees with notice of employer monitoring of phone, email, and internet access/usage. New York’s new law (SB 2628) goes into effect on May 7, 2022. New York joins Connecticut and Delaware , whose laws are already in effect. Unfortunately for employers, the three laws differ with respect to what is covered, when and how employers are to notify employees, and the amount of civil penalties.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

OpenText Information Management
NOVEMBER 17, 2021
This is a time to be bold. To go all in. Be Digital. In my keynote yesterday at OpenText World 2021, I revealed how the world’s best-run organizations are choosing to go all-in on digital. They are using Information Management to solve the challenges of today’s global market, respond to disruption, build stronger communities and … The post OpenText World 2021–The Future of Growth Is Inclusive, Sustainable & Digital appeared first on OpenText Blogs.

Dark Reading
NOVEMBER 17, 2021
Researchers share their findings on the current zero-day market and how criminals' strategies may shift in the future.

Unwritten Record
NOVEMBER 17, 2021
Still taken from 111-WF-25, The Hidden Army. Sometimes films in our holdings stand out for their entertainment value in addition to their historical value, The Hidden Army is one such film. When I came across it looking for another item, it stood out because of the unique way it covers a common topic in propaganda films of World War II, mobilizing women war workers.

Dark Reading
NOVEMBER 17, 2021
Effort part of President Biden’s executive order to improve the nation’s sybersecurity.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Troy Hunt
NOVEMBER 17, 2021
Like most of my good ideas, this one came completely by accident. The other day I was packaging up some swag to send to the winner of my impromptu best "Anonymous" meme competition and I decided to share the following tweet: Time to ramp up the 3D @haveibeenpwned printing too, been giving away a heap of these! pic.twitter.com/ffZpM5aZtx — Troy Hunt (@troyhunt) November 14, 2021 And I was promptly hit by many, many requests for 3D printed HIBP logos.

Dark Reading
NOVEMBER 17, 2021
EU officials and others previously had blamed Russia's intelligence operations for the so-called Ghostwriter campaign.

Archive-It
NOVEMBER 17, 2021
by the Archive-It Team. Archives Unleashed and Archive-It continue our collaborative work integrating Archives Unleashed Cloud’s analytical tools with Archive-It’s web archiving platform in support of web archival research at scale. After several iterations guided by feedback from Archives Unleashed and Archive-It stakeholders, our combined team efforts have resulted in further functionality, dependability, and accessibility of the prototype.

Dark Reading
NOVEMBER 17, 2021
Biometric authentication innovator eliminates password-based account takeover and enables PSD2 Strong Customer Authentication while preserving user privacy.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Archive-It
NOVEMBER 17, 2021
Nov 17, 2021. by Peggy Lee, Product Manager. We invite you to join a webinar led jointly by the Internet Archive (IA) and the Center for Open Science (COS). Researchers, communities, and stakeholders alike are aligning on the need for and the importance of open infrastructure for supporting the production, distribution, and stewardship of public research.

Dark Reading
NOVEMBER 17, 2021
Yes, extended detection and response is possible without endpoint detection and response, but here's why having both is helpful.

Krebs on Security
NOVEMBER 17, 2021
The CEO of a South Carolina technology firm has pleaded guilty to 20 counts of wire fraud in connection with an elaborate network of phony companies set up to obtain more than 735,000 Internet Protocol (IP) addresses from the nonprofit organization that leases the digital real estate to entities in North America. In 2018, the American Registry for Internet Numbers (ARIN), which oversees IP addresses assigned to entities in the U.S., Canada, and parts of the Caribbean, notified Charleston, S.C. b
Let's personalize your content