New Standards Set to Reshape Future of Email Security
Dark Reading
JANUARY 7, 2020
Emerging specs and protocols expected to make the simple act of opening an email a less risky proposition

Dark Reading
JANUARY 7, 2020
Emerging specs and protocols expected to make the simple act of opening an email a less risky proposition

Information Management Resources
JANUARY 7, 2020
In the era of artificial intelligence and machine learning, the fundamental and time-tested processes used to validate and monitor analytic solutions have new facets, but remain essentially intact.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JANUARY 7, 2020
Act Quickly and Prioritize the Basics, Experts Recommend Protecting enterprise networks from attackers inevitably boils down to the same thing: Unless organizations get the basics right, they're sitting ducks. That's one top takeaway from experts warning that Iran will likely retaliate after one of its senior military leaders was killed by a U.S. drone strike.
Krebs on Security
JANUARY 7, 2020
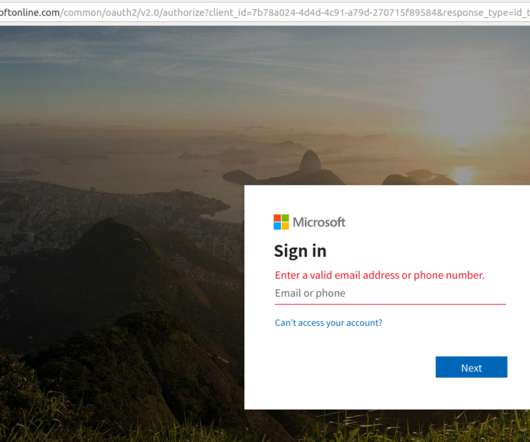
Late last year saw the re-emergence of a nasty phishing tactic that allows the attacker to gain full access to a user’s data stored in the cloud without actually stealing the account password. The phishing lure starts with a link that leads to the real login page for a cloud email and/or file storage service. Anyone who takes the bait will inadvertently forward a digital token to the attackers that gives them indefinite access to the victim’s email, files and contacts — even af

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Data Breach Today
JANUARY 7, 2020
Pulse Secure Says Critical April 2019 Patch Protects Against Sodinokibi Too Attackers are hitting unpatched Pulse Secure VPN servers with Sodinokibi - aka REvil - ransomware, British security researcher Kevin Beaumont warns. Pulse Secure says that although many organizations have installed the critical April 2019 patch, holdouts persist.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Data Breach Today
JANUARY 7, 2020
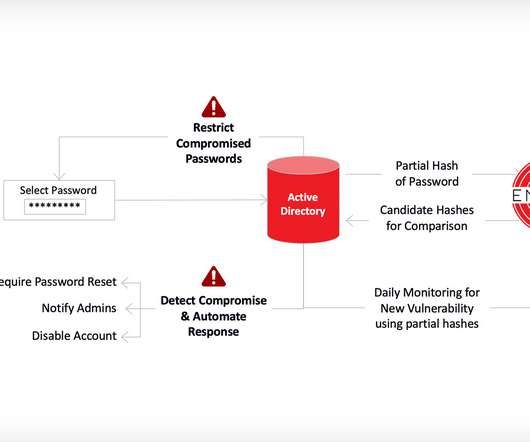
Passwords Remain a Growing Threat Vector Adopting the policies in NIST 800-171 brings multiple security-related benefits, including best practices for data access policies, reduced risk of data breaches and insider threats, and a scalable approach to protecting sensitive data.

CGI
JANUARY 7, 2020
Data monetization in banking: Driving customer centricity and business value. pooja.cs@cgi.com. Tue, 01/07/2020 - 23:50. Banks are awash with data of different types and formats, as well as different levels of detail. While all data is stored, banks use it for different purposes, such as regulatory compliance, customer behavior analysis, and other strategies.
Data Breach Today
JANUARY 7, 2020
In the wake of the killing of an Iranian general in a U.S. drone attack last week, organizations - especially healthcare entities and units of government that have been vulnerable to ransomware attacks - need to be on guard against destructive "wiper" attacks, says Caleb Barlow of CynergisTek.
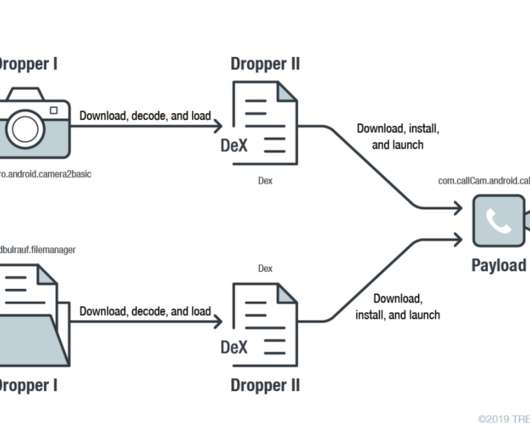
Security Affairs
JANUARY 7, 2020
Security experts have found a malicious app in the Google Play that exploits the recently patched CVE-2019-2215 zero-day vulnerability. Earlier October, Google Project Zero researchers Maddie Stone publicly disclosed a zero-day vulnerability , tracked as CVE-2019-2215 , in Android. Maddie Stone published technical details and a proof-of-concept exploit for the high-severity security vulnerability, seven days after she reported it to the colleagues of the Android security team.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
JANUARY 7, 2020
Deal Will Increase Accenture Security's Managed Services Offerings Accenture plans to buy the former Symantec Cyber Security Services business from Broadcom for an undisclosed sum, the two companies announced Tuesday. The deal comes only five months after Broadcom paid $10.7 billion for Symantec's entire enterprise security division.

Jamf
JANUARY 7, 2020
Put in a little bit of time now to save a lot of time later: prepare for growth in 2020 with Jamf Now.

Data Breach Today
JANUARY 7, 2020
Private Equity Firm Expects to Close Deal in February Private equity firm Insight Partners plans to acquire yet another security company: This time it's IoT security startup Armis. Find out the substantial value of the all-cash deal.

Dark Reading
JANUARY 7, 2020
The top-three carmakers sell only connected vehicles in the United States - and other manufacturers are catching up - creating a massive opportunity for attacks, which black-hat hackers are not overlooking.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Security Affairs
JANUARY 7, 2020
Monika Bickert, Facebook for global policy management, announced that Facebook will ban deepfake videos and manipulated content. Facebook has announced it will ban deepfake videos, which are media that take a person in an existing image or video and replace them with someone else’s likeness using artificial neural networks. Monika Bickert, Facebook vice-president for global policy management, explained that even if these videos are still rare on the Internet, their use is increasing increa

Threatpost
JANUARY 7, 2020
Despite the difficulties of identifying deepfakes, social media sites are recognizing the need to crack down on the manipulated, misleading videos.

Security Affairs
JANUARY 7, 2020
Google has recently disabled all Xiaomi smart home integrations on Nest Hub after being informed that some users could access other people’s camera feeds. . On January 1st, 2020, a Reddit user (‘/u/Dio-V’) posted a discussion revealing that Nest Hub was able to access feeds from other Xiaomi cameras. As proof of the issue, the user shared screenshots of other cameras’ feed that he received on his Xiaomi Mijia 1080p Smart IP Security Camera.

Threatpost
JANUARY 7, 2020
Researchers suspect the cybercriminals attacked using an unpatched critical vulnerability in the company's seven Pulse Secure VPN servers.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
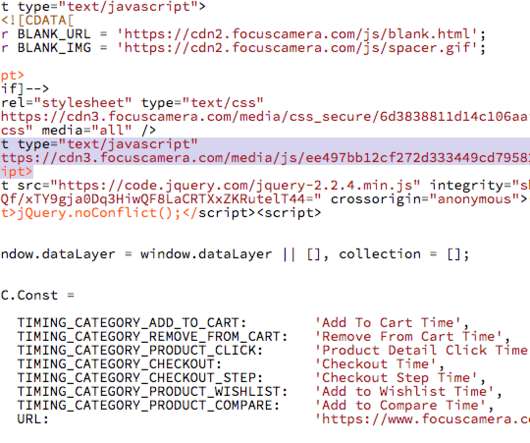
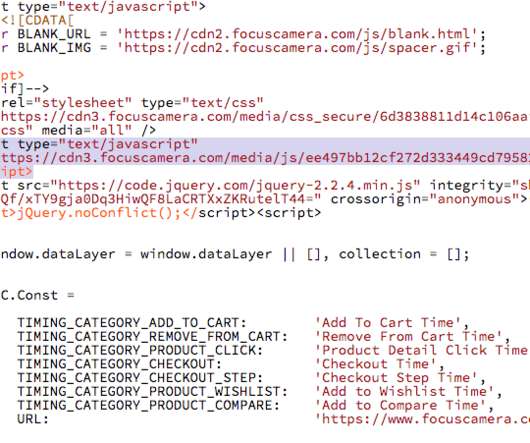
Security Affairs
JANUARY 7, 2020
A new MageCart attack made the headlines, this time the gang compromised the website of popular Focus Camera. The Magecart group has compromised the website of the photography and imaging retailer Focus Camera. The hack took place last year, the hacker planted a software skimmer on the website to steal payment card data of users that purchased the products on the portal.

Hunton Privacy
JANUARY 7, 2020
In a January 6, 2020 blog post , the Director of the Federal Trade Commission’s Bureau of Consumer Protection reflected on how the FTC has taken action over the past year to strengthen its orders in data security cases. These orders have been a subject of focus for the FTC: in June 2018, the 11th Circuit’s LabMD decision struck down an FTC data security order as unenforceably vague, and the FTC subsequently held a hearing in the course of the FTC’s Hearings on Competition and Consumer Protectio

Security Affairs
JANUARY 7, 2020
Minnesota-based Alomere Health discloses a data leak that exposed personal and medical information of 49,351 patients. Personal and medical information of 49,351 patients of Minnesota-based Alomere Health might have been exposed following the compromise of two employees’ email accounts. Alomere Health is a general medical and surgical hospital in Alexandria, MN, with 127 beds.

Schneier on Security
JANUARY 7, 2020
BusKill is designed to wipe your laptop (Linux only) if it is snatched from you in a public place: The idea is to connect the BusKill cable to your Linux laptop on one end, and to your belt, on the other end. When someone yanks your laptop from your lap or table, the USB cable disconnects from the laptop and triggers a udev script [ 1 , , 3 ] that executes a series of preset operations.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Hunton Privacy
JANUARY 7, 2020
On January 6, 2020, the Federal Trade Commission announced that it granted final approval to a settlement with InfoTrax Systems, L.C. and its former CEO, Mark Rawlins, related to allegations that InfoTrax failed to implement reasonable, low-cost and readily available security safeguards to protect the personal information the company maintained on behalf of its business clients.

Threatpost
JANUARY 7, 2020
Google's first security update of 2020 addressed seven high and critical severity Android flaws.

Dark Reading
JANUARY 7, 2020
Recent US military action in Baghdad could prompt retaliatory attacks against US organizations, it says.

IG Guru
JANUARY 7, 2020
The Data Protection Report provides thought leadership on emerging privacy, data protection and cybersecurity issues, and helps its readers proactively address risks and anticipate next steps in this crucial emerging field. The post Record Retention a key component of privacy and cyber compliance program via bn blogs. appeared first on IG GURU.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

The Schedule
JANUARY 7, 2020
Jay Atherton was a long-time archivist at the Public Archives of Canada. In the Winter 1985-86 issue of Archivaria , he published “ From Life Cycle to Continuum: Some Thoughts on the Records Management – Archives Relationship.” Atherton emphasized the necessity of cooperative work between records managers and archivists to accomplish certain goals: “- ensure the creation of the right records, containing the right information, in the right format; – organize the records

Information Management Resources
JANUARY 7, 2020
To keep pace with the technology it will take to build the modern applications that will power tomorrow’s innovation, developers need a diverse set of tools, languages and frameworks.

Threatpost
JANUARY 7, 2020
It's unclear yet whether the Cupertino giant will assist, given past history of court battles over such incidents.
Let's personalize your content