Wormable Apple iCloud Bug Allows Automatic Photo Theft
Threatpost
OCTOBER 9, 2020
Ethical hackers so far have earned nearly $300K in payouts from the Apple bug-bounty program for discovering 55 bugs, 11 of them critical, during a three-month hack.

Threatpost
OCTOBER 9, 2020
Ethical hackers so far have earned nearly $300K in payouts from the Apple bug-bounty program for discovering 55 bugs, 11 of them critical, during a three-month hack.

Krebs on Security
OCTOBER 9, 2020
A week ago, KrebsOnSecurity broke the news that someone was attempting to disrupt the Trickbot botnet , a malware crime machine that has infected millions of computers and is often used to spread ransomware. A new report Friday says the coordinated attack was part of an operation carried out by the U.S. military’s Cyber Command. Image: Shuttstock.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
OCTOBER 9, 2020
The latest edition of the ISMG Security Report analyzes why clothing retailer H&M was hit with a hefty fine for violating the EU's General Data Protection Rule. Also featured: The coming of age of digital identities; deputy CSO at Mastercard on top priorities for 2021.

National Archives Records Express
OCTOBER 9, 2020
Every four years, the Federal Government moves into transition mode. No matter the outcome of the Presidential election, the Government enters a time of transition for senior staff across agencies. The Partnership for Public Service (PPS) Center for Presidential Transition produced a report last year highlighting the need for effective pre-election planning and preparation for significant turnover among the highest-level Government positions. .

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
OCTOBER 9, 2020
Judge Says Cisco's Own Documents Showed It Infringed on 4 Centripetal Networks Patents Why did Cisco, one of the world's largest and most successful networking companies, have to pay more than $2.6 billion in damages? A judge found that it infringed on four patents held by network security firm Centripetal Networks.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
OCTOBER 9, 2020
Websites Were Linked to Islamic Revolutionary Guard Corps The U.S. Justice Department has seized 92 domains that Iran's Islamic Revolutionary Guard Corps was using to support a global disinformation campaign. This was the latest in a series of steps to crack down on Iran's interference activities.

Data Protection Report
OCTOBER 9, 2020
On September 11, 2020, the German Datenschutzkonferenz (DSK), the joint body of the German data protection authorities, published its position on the use of thermal cameras and electronic temperature checks in the context of the COVID-19 pandemic. Despite voicing general criticisms of body temperature checking in the context of COVID-19, the DSK stated that it considers the use of thermal cameras in the work place to be admissible, provided that the requirements of data protection by design laid

Data Breach Today
OCTOBER 9, 2020
Kaspersky: 'MontysThree' Uses Detection Evasion Techniques A hacking group is taking aim at industrial targets in an ongoing cyberespionage campaign, security firm Kaspersky reports. The group, dubbed "MontysThree," uses a variety of techniques, including steganography, to avoid detection.

Threatpost
OCTOBER 9, 2020
Immersive Labs Researcher takes advantage of lax Fitbit privacy controls to build a malicious spyware watch face.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
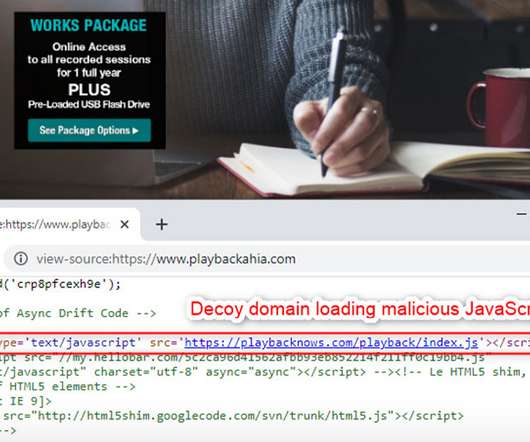
Data Breach Today
OCTOBER 9, 2020
Malwarebytes Says PlayBack Now Customer Sites Compromised While most payment card skimming attacks zero in on ecommerce sites for consumers, a newly discovered attack targeted PlayBack Now, an online video conferencing firm, Malwarebytes reports.

Security Affairs
OCTOBER 9, 2020
Cisco fixed three high-severity flaws in Webex video conferencing system, Video Surveillance 8000 Series IP Cameras and Identity Services Engine. Cisco has addressed three high-severity flaws and eleven medium-severity vulnerabilities in its Webex video conferencing system, Video Surveillance 8000 Series IP Cameras and Identity Services Engine. The most severe of these vulnerabilities is a Remote Code Execution and Denial of Service issue in Cisco’s Video Surveillance 8000 Series IP Cameras.

Data Breach Today
OCTOBER 9, 2020
Case Points to Need to Mitigate the Risks Posed by Insiders A recent incident at a Canadian hospital involving a vendor's former employee who allegedly stole patient records in an attempt to extort money after being laid off illustrates the complex insider threats organizations face.

Troy Hunt
OCTOBER 9, 2020
It's a bit of a mega one this week running over the 1-hour mark, but there's been an awful lot happen during the last week that I reckon is of interest. There's a decidedly adult theme running across the topics not by design, but just by pure coincidence between the Grindr incident, a query I got regarding erasing one's adult website browsing history and the IoT male chastity device full of security holes and potential requiring a grinder (not Grindr!

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
OCTOBER 9, 2020
Insights on Training, Recruitment and How to Get the Most Out of Your Current Tools There's a saying at Rocket Software: "Legacy powers legendary." As vice president and CISO, Adam Glick uses training, technology and recruitment to get similar performance from his ever-evolving cybersecurity team.

Dark Reading
OCTOBER 9, 2020
Microsoft reports a new campaign leveraging the critical Zerologon vulnerability just days after nation-state group Mercury was seen using the flaw.

Security Affairs
OCTOBER 9, 2020
Microsoft warns of Android ransomware that activates when you press the Home button. Microsoft spotted a new strain of Amdroid ransomware tracked as MalLocker.B that activates when the users press the Home button. Researchers from Microsoft spotted a new strain of Android ransomware that abuses the mechanisms behind the “incoming call” notification and the “Home” button to lock the screen on the victim’s device.

Dark Reading
OCTOBER 9, 2020
In recent weeks, Emotet has emerged as the most common form of ransomware. Managing the risk involves starts with understanding the way it works.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

eSecurity Planet
OCTOBER 9, 2020
Your SD-WAN solution comes with built-in security, but it's likely not enough to meet enterprise security requirements. Here are some next steps.

Dark Reading
OCTOBER 9, 2020
So far, the company has doled out $288,000 to five researchers who, in three months, found 55 vulnerabilities in its corporate infrastructure.

Security Affairs
OCTOBER 9, 2020
NATO Chief calls for a new strategic to mitigate the risks related to the threats to the rising technologies, new forms of terrorism, and the role of China. The rapid and continuous changes in our society needs to be properly addressed, NATO warns, NATO Chief call for a new strategic to address the global rise of new technologies, the evolution of terrorism and role of China in the global politics.

Threatpost
OCTOBER 9, 2020
Facebook bounty hunters will be placed into tiers by analyzing their score, signal and number of submitted bug reports -- which will dictate new bonus percentages.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Security Affairs
OCTOBER 9, 2020
The hacker who shared with the ISIS personal data of more than 1,300 U.S. government and military personnel will remain in a federal prison. Ardit Ferizi , aka Th3Dir3ctorY, is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel. Ferizi is the first man charged with cyber terrorism that was extradited to the US early 2016.

Data Matters
OCTOBER 9, 2020
Recent changes to Chinese law have broad implications on cross-border data transfer in the course of investigations conducted by non-Chinese regulators. Clients work closely with counsel to navigate potential legal landmines in any defense of an investigation involving data from China. Just over six months ago, on March 24, 2020, the People’s Republic of China’s (PRC) revised Securities Law (revised on December 28, 2019) (???????????

OpenText Information Management
OCTOBER 9, 2020
This blog is co-authored by Alison Clarke and Sandi Nelson. Having the right partners by your side is crucial as your organization digitally transforms for the new equilibrium. On the journey toward cloud content management, Forrester says companies should look for vendors that offer flexibility, migration support, and a broad range of functionality.

Dark Reading
OCTOBER 9, 2020
Managed service providers are increasingly becoming the launching pad of choice for ransomware and other online malfeasance.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

OpenText Information Management
OCTOBER 9, 2020
OpenText will be hosting our major conference of the year, OpenText World, between 26th and 29th October 2020. COVID-19 has transformed how many companies are engaging with their customers and OpenText is no different, with this year’s OpenText World being hosted digitally. Even though our event may be digital this year, it will still deliver an unrivaled experience for those companies looking … The post Rethinking supply chains at OpenText World appeared first on OpenText Blogs.

eSecurity Planet
OCTOBER 9, 2020
We review the top vendors in threat intelligence, which has become a critical security tool as the volume and complexity of threat vectors grows.

Dark Reading
OCTOBER 9, 2020
Like most such mobile malware, the new one doesn't encrypt data but attempts to make an infected system impossible to use, Microsoft says.
Let's personalize your content