Russia Is Being Hacked at an Unprecedented Scale
WIRED Threat Level
APRIL 27, 2022
From “IT Army” DDoS attacks to custom malware, the country has become a target like never before.

WIRED Threat Level
APRIL 27, 2022
From “IT Army” DDoS attacks to custom malware, the country has become a target like never before.
Data Breach Today
APRIL 27, 2022
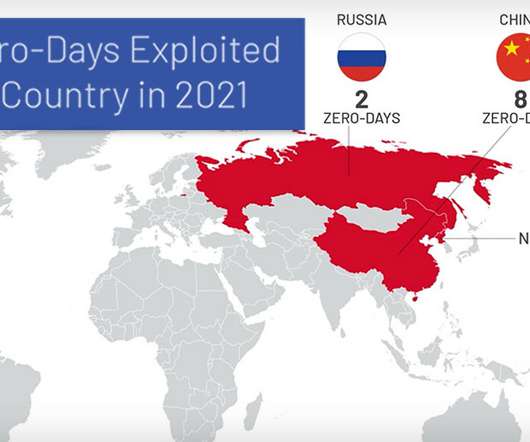
80 Zero-Day Vulnerabilities - a Record Number - Were Exploited in the Wild in 2021 The median number of days an attacker dwells in a system before detection fell from 24 days in 2020 to 21 days in 2021, according to a Mandiant report. The biggest year-on-year decline in median dwell time occurred in the APAC region, where it dropped from 76 days in 2020 to 21 days in 2021.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
APRIL 27, 2022
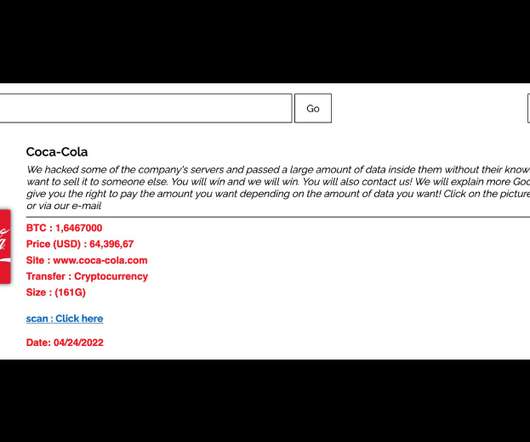
The Stormous ransomware group is offering purportedly stolen Coca-Cola data for sale on its leak site, but the soda giant hasn't confirmed that the heist happened.

Data Breach Today
APRIL 27, 2022
6 Russian Military Intelligence Agents Charged With Launching NotPetya Destruction The U.S. government on Tuesday announced a reward of up to $10 million for information pertaining to six alleged Russian military hackers tied to the 2017 NotPetya destructive malware campaign. The malware spread globally, causing commercial damage of up to $10 billion.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
APRIL 27, 2022
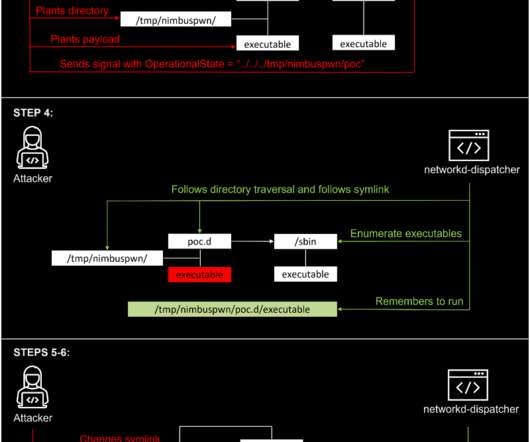
Microsoft disclosed two Linux privilege escalation flaws, collectively named Nimbuspwn, that could allow conducting various malicious activities. The Microsoft 365 Defender Research Team has discovered two Linux privilege escalation flaws (tracked as CVE-2022-29799 and CVE-2022-29800) called “Nimbuspwn,” which can be exploited by attackers to conduct various malicious activities, including the deployment of malware. “The vulnerabilities can be chained together to gain root priv
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
APRIL 27, 2022
A new report suggests that a small but vibrant group of smartphones hackers may be challenging the world's most digitally restrictive regime.

Data Breach Today
APRIL 27, 2022
$44.5 Million Deal Aims to Expand Visibility for Tenable's Vulnerability Management Tenable has agreed to purchase startup Bit Discovery for $44.5 million to help companies discover, attribute and monitor assets on the internet. The deal will allow Tenable to identify vulnerable internet-facing assets that could be attacked.

Dark Reading
APRIL 27, 2022
Internet-facing zero-day vulnerabilities were the most commonly used types of bugs in 2021 attacks, according to the international Joint Cybersecurity Advisory (JCSA).
Data Breach Today
APRIL 27, 2022
Stormous Ransomware Group Says It Exfiltrated 161GB of Critical Data Ransomware group Stormous, in a Telegram post on Monday, said that it has breached and exfiltrated 161GB worth of critical data from beverage manufacturing giant Coca-Cola. The soft drink company has told Information Security Media Group that it is investigating the claim.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
APRIL 27, 2022
The German wind turbine giant Deutsche Windtechnik was hit by a targeted cyberattack earlier this month. German wind turbine giant Deutsche Windtechnik announced that some of its systems were hit by a targeted professional cyberattack earlier this month. The attack took place during the night between April 11 and 12, the company switched off remote data monitoring connections to the wind turbines for security reasons.

Data Breach Today
APRIL 27, 2022
WhiteHat Security Excels at Defending Web Applications in Production Environments Synopsys has agreed to buy WhiteHat Security from NTT Security for $330 million to defend web applications in production environments in an automated, scalable fashion. WhiteHat will provide continuous security testing for hundreds or thousands of apps on live websites in a production-safe manner.

Security Affairs
APRIL 27, 2022
The U.S. government offers up to $10 million for info that allows to identify or locate six Russian GRU hackers who are members of the Sandworm APT group. The US Department of State is offering up to $10 million for info that allows to identify or locate six Russian GRU hackers who are members of the Sandworm APT group. The reward is covered by the Rewards for Justice program of the US government, which rewards people that can share information that can allow to identify or locate foreign gover

Data Breach Today
APRIL 27, 2022
A Chapter of the New Book 'Heuristic Risk Management' by Michael Lines Michael Lines is working with ISMG to promote awareness of the need for cyber risk management, and the CyberEdBoard is posting draft chapters from his upcoming book, "Heuristic Risk Management: Be Aware, Get Prepared, Defend Yourself." This chapter is titled "Recognize Their Attacks.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Schneier on Security
APRIL 27, 2022
Both Google and Mandiant are reporting a significant increase in the number of zero-day vulnerabilities reported in 2021. Google: 2021 included the detection and disclosure of 58 in-the-wild 0-days, the most ever recorded since Project Zero began tracking in mid-2014. That’s more than double the previous maximum of 28 detected in 2015 and especially stark when you consider that there were only 25 detected in 2020.

Data Breach Today
APRIL 27, 2022
New 'Rockets' Aim to Grow the Cloud Security, Email Security and MDR Businesses Check Point is aggressively expanding its salesforce and standing up "rockets" focused on emerging technology areas to land more customer deals outside network security. The company will couple 25% growth in its salesforce with dedicated investments around cloud security, email security and MDR.

Thales Cloud Protection & Licensing
APRIL 27, 2022
Anatomy of a Quantum Attack. divya. Thu, 04/28/2022 - 06:15. Next-generation cyberattacks are often summarized as ransomware, man-in-the-middle, brute-force, phishing, insider, or malware attacks. Each present a unique set of challenges and require equally powerful next-generation cyber security. But another, far more damaging, attack vector is looming – quantum attack.

Data Breach Today
APRIL 27, 2022
In this episode of "Cybersecurity Unplugged," Prachee Kale - a pioneer of CyberEd.io's Think.Design.Cyber. - discusses the need for systems and design thinking in cybersecurity marketing, how to tell your marketing story, and how systems and design thinking can lead to creative solutions.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
APRIL 27, 2022
Conti ransomware gang continues to target organizations worldwide despite the massive data leak has shed light on its operations. Researchers from Secureworks state that the Conti ransomware gang, tracked as a Russia-based threat actor Gold Ulrick, continues to operate despite the recent data leak on its internal activities. The group’s activity returned to the levels that represented a peak in 2021, the gang rapidly reacted to the public disclosure of its communications, source code, and

Data Breach Today
APRIL 27, 2022
Forrester Researchers on Using AX to Improve the SOC and Security Analyst Workflow Forrester analysts Allie Mellon and Jeff Pollard discuss their new research on the analyst experience, or AX. AX involves how security analysts perceive their interactions with security products, services and processes, and Mellon and Pollard say it can improve the SOC and security analyst workflow.
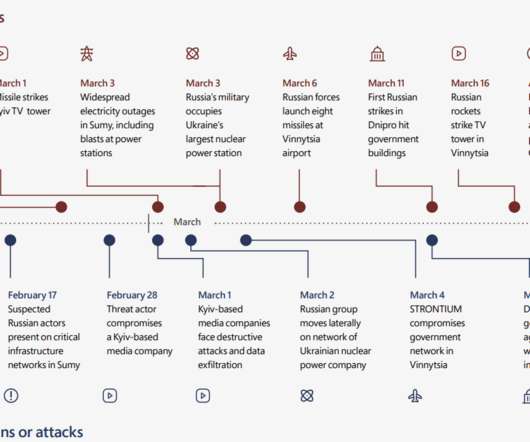
Security Affairs
APRIL 27, 2022
Microsoft revealed that Russia launched hundreds of cyberattacks against Ukraine since the beginning of the invasion. Microsoft states that at least six separate Russia-linked threat actors launched more than 237 operations against Ukraine starting just before the invasion. The cyber attacks included destructive wipers that were used to target critical infrastructure in a hybrid war against Ukraine.

Dark Reading
APRIL 27, 2022
What 5,800+ pentests show us: Companies have been struggling with the same known and preventable security bugs year over year. Bandwidth stands at the heart of the problem.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Threatpost
APRIL 27, 2022
Four months after the critical flaw was discovered, attackers have a massive attack surface from which they can exploit the flaw and take over systems, researchers found.

Dark Reading
APRIL 27, 2022
The war in Ukraine appears to have triggered a change in mission for the APT known as Bronze President (aka Mustang Panda).

Threatpost
APRIL 27, 2022
The Botnet appears to use a new delivery method for compromising Windows systems after Microsoft disables VBA macros by default.

Dark Reading
APRIL 27, 2022
The four-year-old firm, started by two industry veterans, focuses on gaining visibility into Internet-facing services as more companies seek insight into what attackers see.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

erwin
APRIL 27, 2022
Voting is going on now, and ends on May 11! If you love our products, please vote. We need your help! Year after year, customers vote Quest® products as their #1 choice in database solutions. It’s voting time again. Please help us keep our #1 position in 2022. This is a reader’s choice award, and that means winners are determined by the number of votes received — by loyal customers like you.

Dark Reading
APRIL 27, 2022
The startup is the latest company to try to solve the problem of organizing and sharing secrets.

Jamf
APRIL 27, 2022
A patch to Windows Server released in November 2021 to fix CVE-2021-42287 inadvertently broke binding of macOS devices to Microsoft Active Directory. Microsoft released a new patch on April 12, 2022 to the release channel for Windows Server to solve the problem. Administrators are encouraged to install and vigorously test a development environment if your organization binds macOS devices to Active Directory.
Let's personalize your content