COVID-19-Related Fraud: 474 Charged So Far
Data Breach Today
MARCH 26, 2021
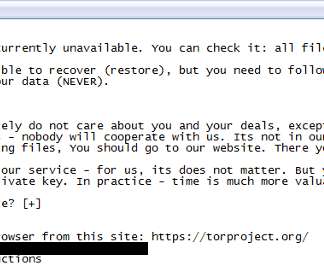
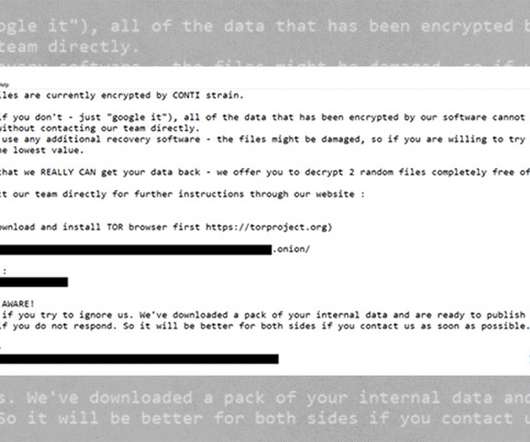
Prosecutors: Fraudsters Tried to Swindle More Than $569 Million Over 12 Months Over the last 12 months, federal prosecutors have charged 474 suspects with trying to steal more than $569 million through COVID-19-related fraud schemes, including attempts to swindle the Paycheck Protection Program for small businesses.









































Let's personalize your content