Cybercrime: Ransomware Attacks Surging Once Again
Data Breach Today
APRIL 28, 2022
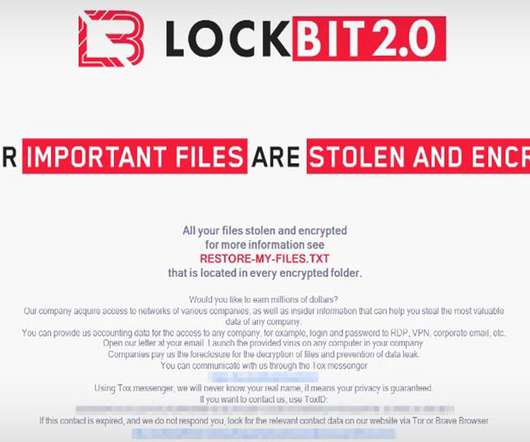
Lockbit, Conti, Hive and Alphv/BlackCat Tied to Greatest Number of Known Victims Ransomware attacks have come storming back after experiencing their typical end-of-the year decline. Security researchers report that the greatest number of known victms has been amassed by Lockbit, followed by Conti, Hive and Alphv/BlackCat.







































Let's personalize your content