T-Mobile Breached Again; Lapsus$ Behind the Attack
Data Breach Today
APRIL 23, 2022
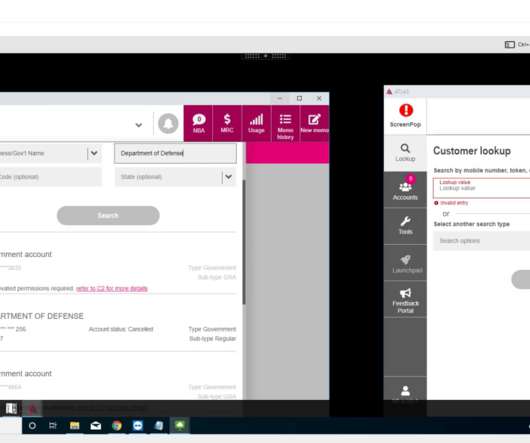
Company Says No Sensitive Customer or Government Information Leaked The US telecom carrier T-Mobile has confirmed that the Lapsus$ ransomware group has breached its internal network by compromising employee accounts. The company says hackers did not steal any sensitive customer or government information during the incident.











Let's personalize your content