NFTs Are a Privacy and Security Nightmare
WIRED Threat Level
APRIL 5, 2022
The blockchain isn’t as “anonymous” as you might think.

WIRED Threat Level
APRIL 5, 2022
The blockchain isn’t as “anonymous” as you might think.

Data Breach Today
APRIL 5, 2022
Witnesses at Hearing Also Discuss Role of Government in Security Incident Response A water trade association, at a congressional hearing Tuesday, urged the federal government to institute minimum cybersecurity standards for water systems. This comes as water providers see a big increase in the risk they face by connecting their legacy machines to the internet.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
APRIL 5, 2022
As the dust settles following the recently disclosed hack of NewsCorp , important lessons are emerging for the cybersecurity and journalism communities. Related: How China challenged Google in Operation Aurora. The Chinese government is well known for its censorship– and frequent harassment and intimidation of foreign journalists. These are the foremost reasons China is ranked fourth worst globally regarding press freedoms.

Data Breach Today
APRIL 5, 2022
Firmware Updated; Users Advised to Patch to Avoid DDoS Attacks A new ongoing malware campaign is currently being conducted in the wild, targeting unpatched TOTOLINK routers. By leveraging a newly released exploit code, threat actors can use this variant of the Mirai botnet, called Beastmode, to potentially infect vulnerable devices.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
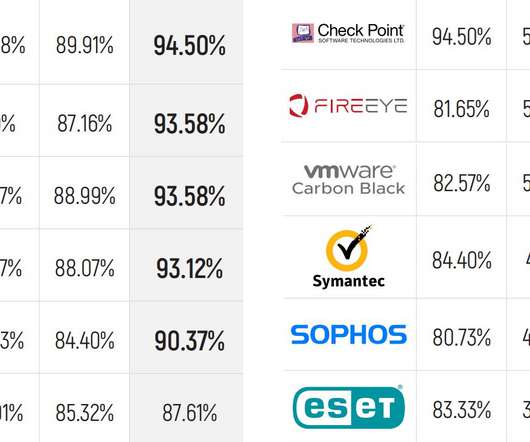
eSecurity Planet
APRIL 5, 2022
MITRE Engenuity has released the latest round of its ATT&CK endpoint security evaluations, and the results show some familiar names leading the pack with the most detections. The MITRE evaluations are unique in that they emulate advanced persistent threat (APT) and nation-state hacking techniques, making them different from tests that might look at static malware samples, for example.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Dark Reading
APRIL 5, 2022
Security features to come include a TPM-like security processor for protecting artifacts that a computer uses during the secure boot-up process, as well as a control for blocking unsigned and untrusted apps.

OpenText Information Management
APRIL 5, 2022
“Going paperless” is a commonly stated goal in a school district’s digital transformation plan, but it’s just the beginning of a journey toward the increased efficiency, effectiveness and modern work culture that technology can bring to bear. Freeing up physical space and reducing costs are certainly benefits, but the real gains school districts typically seek … The post It’s not just about going paperless appeared first on OpenText Blogs.

Schneier on Security
APRIL 5, 2022
Brian Krebs has a detailed post about hackers using fake police data requests to trick companies into handing over data. Virtually all major technology companies serving large numbers of users online have departments that routinely review and process such requests, which are typically granted as long as the proper documents are provided and the request appears to come from an email address connected to an actual police department domain name.

Threatpost
APRIL 5, 2022
This fresh malware strain extends the functionality of typical trojans with advanced functionality and a series of modules for launching various types of threat activity.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
APRIL 5, 2022
Anonymous continues to support Ukraine against the Russian criminal invasion targeting the Russian military and propaganda. Anonymous leaked personal details of the Russian military stationed in Bucha where the Russian military carried out a massacre of civilians that are accused of having raped and shot local women and children. Leaked data include names, ranks and passport details of Russians serving in the 64 Motor Rifle Brigade which occupied Bucha prior to March 31.

KnowBe4
APRIL 5, 2022
[EYE OPENER] A Lack of Employee Cyber Hygiene is the Next Big Threat. Email not displaying? | View Knowbe4 Blog. CyberheistNews Vol 12 #14 | Apr. 5th., 2022. [EYE OPENER] A Lack of Employee Cyber Hygiene is the Next Big Threat. A new report suggests that everything from endpoints, to passwords, to training, to security policies, to a lack of awareness is all contributing to much higher risk of cyberattack.
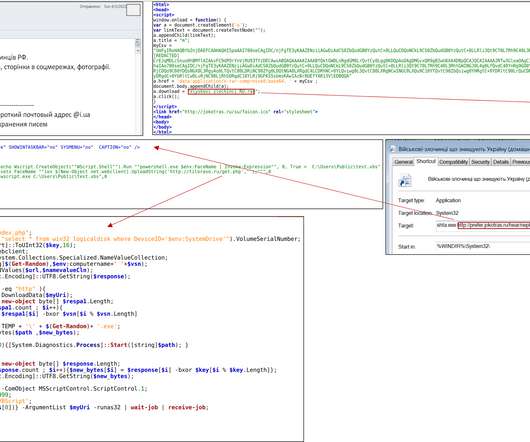
Security Affairs
APRIL 5, 2022
Ukraine CERT-UA spotted a spear-phishing campaign conducted by Russia-linked Armageddon APT targeting local state organizations. Ukraine CERT-UA published a security advisory to warn of spear-phishing attacks conducted by Russia-linked Armageddon APT (aka Gamaredon , Primitive Bear, Armageddon, Winterflounder, or Iron Tilden) targeting local state organizations.

KnowBe4
APRIL 5, 2022
Cybercriminals Groups and “as a Service” threat actor affiliates alike seem to be doing well, according to a new report on the state of ransomware from Palo Alto Networks’ Unit42.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

WIRED Threat Level
APRIL 5, 2022
More than just a market for illegal drugs, the dark-web site allowed criminals to launder or cash out hundreds of millions in stolen cryptocurrencies.

Dark Reading
APRIL 5, 2022
Remain calm, maintain control, and triage responses appropriately to ensure that the organization can remain resilient against threats during this crisis and through others to come.

IG Guru
APRIL 5, 2022
Mile High Denver ARMA 2022 Spring Seminar is Almost here. The seminar has been pre-approved for 4 IGP CEUs and 5 CRM CEUs Register In addition to the spring seminar right around the corner, the MHD Chapter is raising money to help the families of the Marshall Fire that affected the Boulder community on December 30th, 2021. […]. The post Mile High Denver ARMA 2022 Spring Seminar on April 19 appeared first on IG GURU.

Dark Reading
APRIL 5, 2022
Mandiant has now tied the group to at least eight unattributed clusters of activity targeting organizations across various industries and regions.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
APRIL 5, 2022
The U.S. CISA added the recently disclosed remote code execution (RCE) vulnerability Spring4Shell to its Known Exploited Vulnerabilities Catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the recently disclosed CVE-2022-22965 (aka Spring4Shell , CVSS score: 9.8) flaw in the Spring Framework, along with three other issues, to its Known Exploited Vulnerabilities Catalog.

KnowBe4
APRIL 5, 2022
The group behind the recent attacks on Okta, NVIDIA, and Microsoft may be moving on to less-prominent organizations, using their data destruction extortion model on new victims.

Dark Reading
APRIL 5, 2022
Nudge Security plans a general launch of its cloud-based service later this year.

KnowBe4
APRIL 5, 2022
It appears that the use of Microsoft CHM files is gaining popularity, and from the way this latest attack works, it’s a rather ingenious and flexible method that could become more prevalent.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Threatpost
APRIL 5, 2022
The popular underground market traded in drugs, stolen data, forged documents and more -- raking in billions in Bitcoin.

KnowBe4
APRIL 5, 2022
Social engineering continues to be a core component of the Iranian government’s hacking operations, according to researchers at Recorded Future.

Dark Reading
APRIL 5, 2022
The group is targeting the biggest weak spot in most security postures: finding anomalous behavior by authorized entities.

Jamf
APRIL 5, 2022
A new vulnerability has been discovered within the Java Spring Framework which may allow for remote execution on a server.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
APRIL 5, 2022
But "old habits are hard to break," with 48% of developers still shipping code with vulnerabilities.

Jamf
APRIL 5, 2022
April is designated as Distracted Driving Awareness Month in the United States, so it’s a good time to think about what counts as distracted driving and how to meaningfully avoid it. Featuring an integration with Jamf MDM solutions, LifeSaver Mobile is a digital solution that can help keep employees safe on the road.

Dark Reading
APRIL 5, 2022
Come up with a clever caption, and our panel of experts will reward the winner with a $25 Amazon gift card.
Let's personalize your content