Data Breach Reports Rise as Supply Chain Attacks Surge
Data Breach Today
OCTOBER 8, 2021
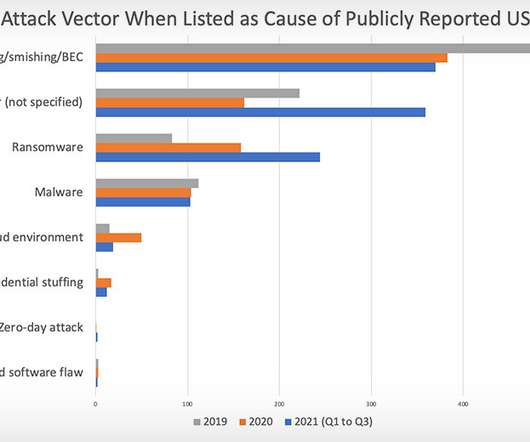
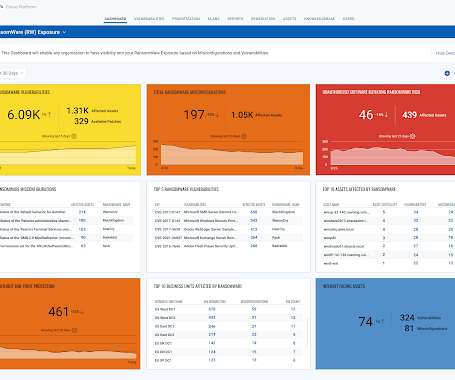
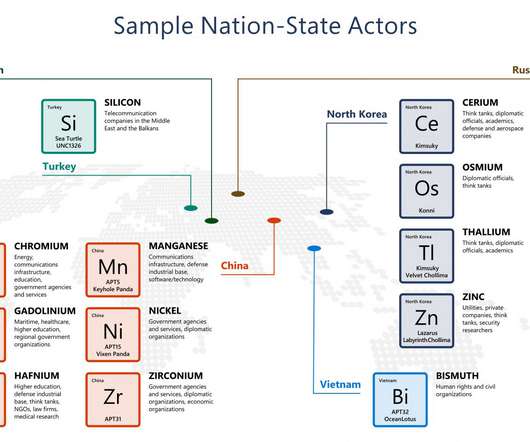
US Breach Notification Transparency Declining, Identity Theft Resource Center Warns The number of breach reports filed by U.S. organizations looks set to break records, as breaches tied to phishing, ransomware and supply chain attacks keep surging, the Identity Theft Resource Center warns. It says that there's also been a rise in tardy breach notifications containing little detail.





































Let's personalize your content