Law Firms Race to File Phishing Breach Lawsuits
Data Breach Today
FEBRUARY 10, 2020
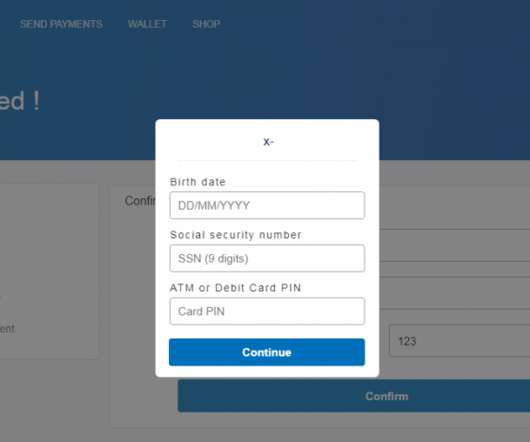
Class Action Suits Would Focus on PIH Health Breach That Affected 200,000 Several law firms are racing to be among the first to file class action lawsuits against PIH Health in the wake of the California-based regional healthcare network reporting last month that a 2019 phishing breach affected nearly 200,000 individuals. Why the rush?





































Let's personalize your content