Microsoft’s Patch Tuesday for March 2023 includes patches for more than 70 vulnerabilities, including zero-day flaws in Outlook and in Windows SmartScreen.
According to Crowdstrike researchers, 40 percent of the patched vulnerabilities are remote code execution flaws, down from 48 percent last month; 31 percent are elevation of privilege flaws, up from almost 16 percent last month; and 22 percent are information disclosure flaws, up from 10 percent last month.
Critical Outlook Zero-Day
The Outlook zero-day, CVE-2023-23397, with a critical CVSS score of 9.8, is being actively exploited. “An attacker who successfully exploited this vulnerability could access a user’s Net-NTLMv2 hash which could be used as a basis of an NTLM Relay attack against another service to authenticate as the user,” the company wrote.
Microsoft warned, “The attacker could exploit this vulnerability by sending a specially crafted email which triggers automatically when it is retrieved and processed by the Outlook client. This could lead to exploitation BEFORE the email is viewed in the Preview Pane.”
Considering the ease of exploitation, Microsoft also recommends the following mitigations in addition to downloading the latest updates:
- Add users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism. Performing this mitigation makes troubleshooting easier than other methods of disabling NTLM. Consider using it for high value accounts such as Domain Admins when possible.
- Block TCP 445/SMB outbound from your network by using a perimeter firewall, a local firewall, and via your VPN settings. This will prevent the sending of NTLM authentication messages to remote file shares.
See the Top Secure Email Gateway Solutions
A Significant Threat
“Given the network attack vector, the ubiquity of SMB shares, and the lack of user authentication required, an attacker with a suitable existing foothold on a network may well consider this vulnerability a prime candidate for lateral movement,” Rapid7 lead software engineer Adam Barnett said.
Tenable senior staff research engineer Satnam Narang said by email that CVE-2023-23397 is likely to be one of the top vulnerabilities of 2023, noting that MDSec researchers have already developed a proof-of-concept exploit for the flaw that requires no user interaction (screenshot below).
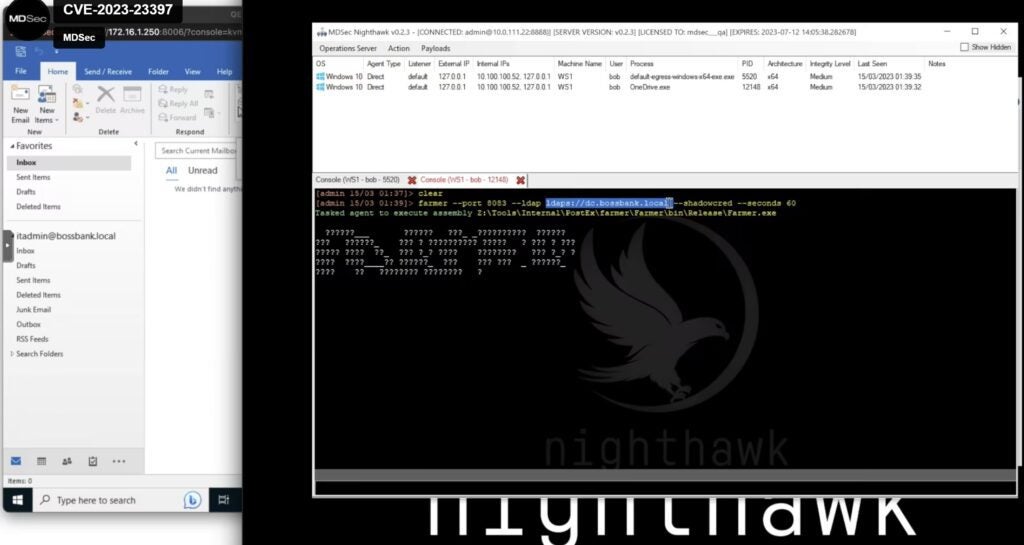
“Additionally, Microsoft confirmed that the flaw had been exploited as a zero day as part of limited attacks against government, transportation, energy, and military targets organizations in Europe by a Russia-based threat actor,” Narang said. “Based on the simplicity by which this vulnerability can be exploited, we believe it’s only a matter of time before it is adopted into the playbooks of other threat actors, including ransomware groups and their affiliates.”
Also read: Ransomware Protection: How to Prevent Ransomware Attacks
SmartScreen Zero-Day
The SmartScreen zero-day, CVE-2023-24880, is also being actively exploited but has a much lower CVSS score of 5.4. “An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging,” Microsoft explained.
“This bug means that some files that come in from outside – for example, downloads or email attachments – don’t get tagged with the right MOTW identifier, so they sneakily sidestep Microsoft’s official security checks,” Sophos’ Paul Ducklin explained in a blog post on the updates.
“Microsoft’s public bulletin doesn’t say exactly what type of file (images? Office documents? PDFs? all of them?) can be infiltrated into your network in this way, but does warn very broadly that “security features such as Protected View in Microsoft Office” can be bypassed with this trick,” Ducklin added.
Two More Critical Flaws
Action1 vice president of vulnerability and threat research Mike Walters highlighted two other critical flaws in a blog post. The first, CVE-2023-23415, is a remote code execution vulnerability in the Internet Control Message Protocol (ICMP) with a CVSS score of 9.8.
“An attacker can use this weakness to send a low-level protocol error, containing a fragmented IP packet within another ICMP packet header, to the target machine,” Walters noted. “To activate the flaw, an application on the target must be connected to a raw socket. This vulnerability could result in remote code execution. The attack is easy to execute and does not require any privileges or user interaction.”
The second, CVE-2023-23392, is a remote code execution vulnerability in the HTTP Protocol Stack, also with a CVSS score of 9.8. “An unauthenticated attacker can exploit this vulnerability by sending a specially crafted packet to a targeted server that utilizes the HTTP Protocol Stack (http.sys) to process packets,” Walters observed. “This can lead to remote code execution, posing a significant security risk.”






