Magniber Ransomware Group Exploiting Microsoft Zero Day
Data Breach Today
MARCH 16, 2023
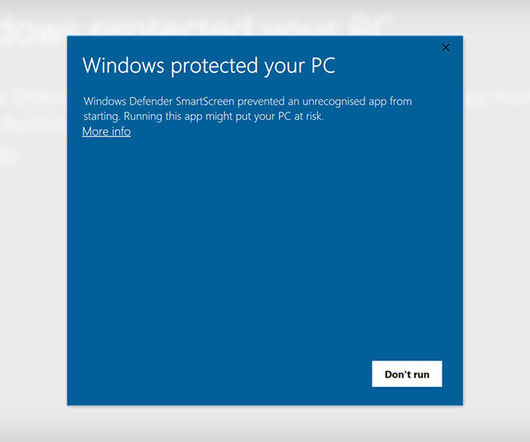
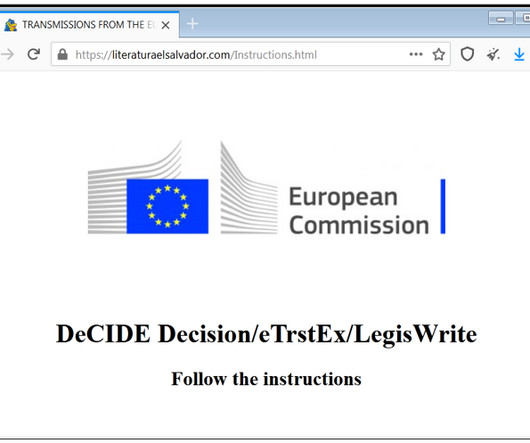
Microsoft Patches Another SmartScreen Signature-Based Vulnerability A financial motivated hacking group has been exploiting a now-patched zero-day vulnerability in the Windows operating system to deliver ransomware. Google Threat Analysis Group attributed the campaign to Magniber ransomware group. Microsoft issued a patch in its March dump of fixes.








































Let's personalize your content