In the Fight Against Cybercrime, Takedowns Are Only Temporary
Dark Reading
DECEMBER 30, 2021
Disrupting access to servers and infrastructure continues to interfere with cybercrime activity, but it's far from a perfect strategy.

Dark Reading
DECEMBER 30, 2021
Disrupting access to servers and infrastructure continues to interfere with cybercrime activity, but it's far from a perfect strategy.

The Last Watchdog
DECEMBER 30, 2021
Workforce management software ( WFM ) is an essential tool companies across industries can use to organize their workforce, track employee work and performance, forecast labor demand, and create schedules for employees. Related: Turning workers into security security sensors. Most, if not all, WFM software is chock full of features that makes managing a workforce more efficient and effortless for top management.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 30, 2021
A previously unknown rootkit, dubbed iLOBleed, was used in attacks aimed at HP Enterprise servers that wiped data off the infected systems. iLOBleed, is a previously undetected rootkit that was spotted targeting the HP Enterprise’s Integrated Lights-Out ( iLO ) server management technology to tamper with the firmware modules and wipe data off the infected systems.

Threatpost
DECEMBER 30, 2021
Expect many more zero-day exploits in 2022, and cyberattacks using them being launched at a significantly higher rate, warns Aamir Lakhani, researcher at FortiGuard Labs.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Security Affairs
DECEMBER 30, 2021
Researchers found several vulnerabilities in third-party encryption software that is used by multiple storage devices from major vendors. Researcher Sylvain Pelissier has discovered that the DataVault encryption software made by ENC Security and used by multiple vendors is affected by a couple of key derivation function issues. An attacker can exploit the flaws to obtain user passwords.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
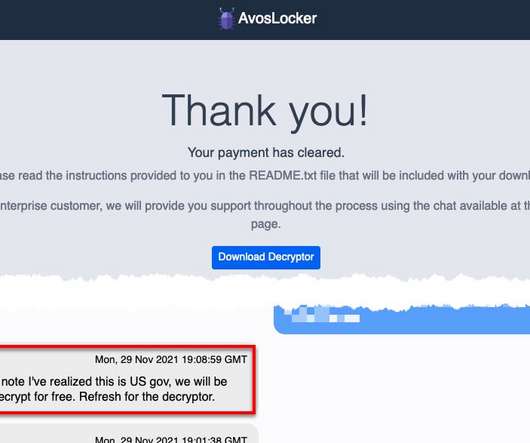
Security Affairs
DECEMBER 30, 2021
The AvosLocker ransomware operators released a free decryptor after they accidentally encrypted the system of US Government entity. The AvosLocker ransomware operation provided a free decryptor after they encrypted the systems of a US government agency. AvosLocker RaaS operators trying to avoid heat after hitting a US government entity by providing them the decryptor for free. pic.twitter.com/zFg7Idj9Zs — ???????

Hunton Privacy
DECEMBER 30, 2021
On December 15, 2021, the New Jersey Acting Attorney General Andrew J. Bruck announced that its Division of Consumer Affairs had reached a $425,000 settlement with New Jersey-based providers of cancer care, Regional Cancer Care Associates LLC, RCCA MSO LLC and RCCA MD LLC (collectively, “RCCA”), over alleged failures to adequately safeguard patient data.

Threatpost
DECEMBER 30, 2021
Researchers from CrowdStrike disrupted an attempt by the threat group to steal industrial intelligence and military secrets from an academic institution.

Troy Hunt
DECEMBER 30, 2021
2021 Dumpster fire? Harsh, but fair and I shall keep this 3D-printed reminder handy and hope I don't end up needing to print a 2022 version! So many times throughout this week's video I came back to that theme. But hey, there was some positive stuff too, not least the bits about some of the wonderful organisations I've worked with this year, bought products from or otherwise just been a big part of my digital life in 2021.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
DECEMBER 30, 2021
Zero trust moves the control pane closer to the defended asset and attempts to tightly direct access and privileges.

eDiscovery Daily
DECEMBER 30, 2021
Collaboration apps, forensic tools, and discovery software are just a few technologies that an attorney must juggle regularly. As old technologies update and new ones emerge, will you adapt or fall behind? At first, keeping up with these changes may seem impossible, but there are multiple steps you can take. Brush up on your knowledge by reading case law, eDiscovery blogs, and regulations on data collection.

IG Guru
DECEMBER 30, 2021
Reimagining Records and Governance – A Personal Odyssey John will be discussing his new book, Immigrant Secrets, the story of a 5-year personal records odyssey to discover what happened to his Italian immigrant grandparents. The only thing he knew growing up was that his grandparents died in the 1930s – only they didn’t. The book is the […].
Let's personalize your content