Hacked: US Commerce and Treasury Departments
Data Breach Today
DECEMBER 14, 2020
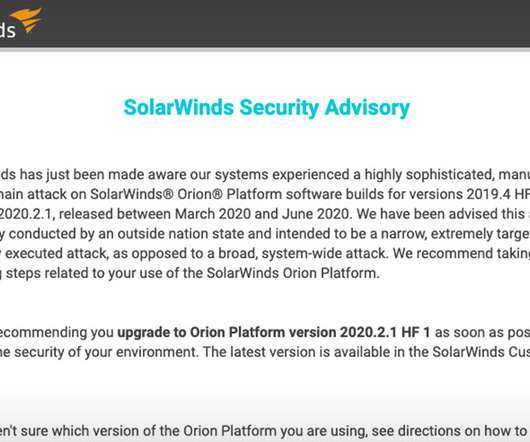
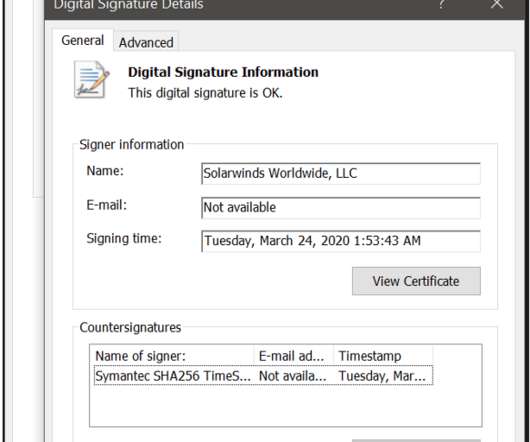
Fellow Victim FireEye Traces Breaches to Trojanized SolarWinds Software Updates The U.S. Commerce Department confirmed on Sunday it had been targeted by hackers, and the U.S. Treasury has also reportedly been struck. The intrusions appear linked to subverted software updates for SolarWinds' Orion network monitoring product, which is widely used by companies and the U.S. government.






































Let's personalize your content