Ransomware Attacks in Healthcare: Are We Seeing a Surge?
Data Breach Today
JUNE 23, 2020
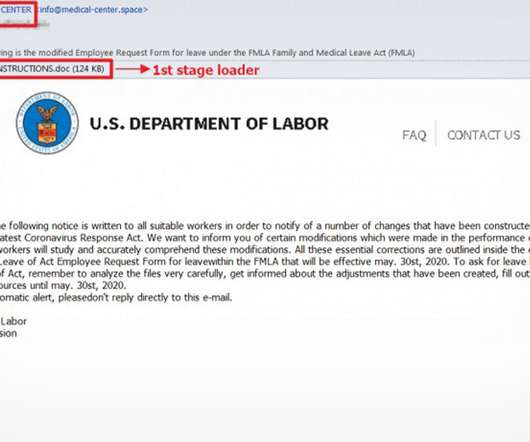
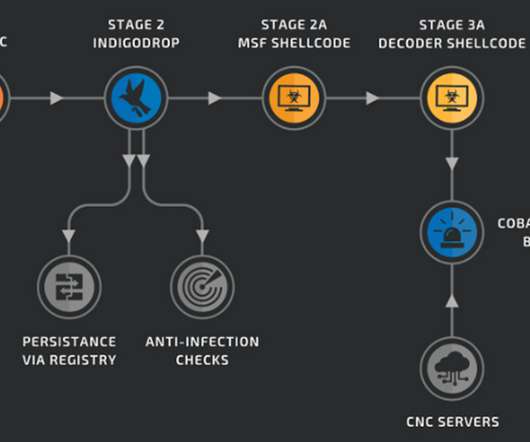
New Risks Could Emerge as More Practices Reopen Four recent cybersecurity incidents that may have involved ransomware demonstrate the ongoing threats facing the sector during the COVID-19 pandemic. They also serve as a warning that extra watchfulness is needed as physicians reopen their clinics.





































Let's personalize your content