Pay Up, Or We’ll Make Google Ban Your Ads
Krebs on Security
FEBRUARY 17, 2020
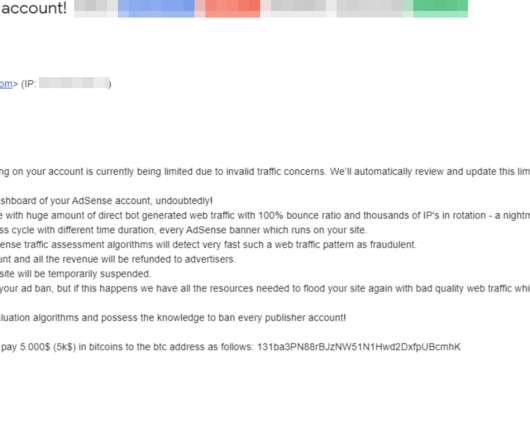
A new email-based extortion scheme apparently is making the rounds, targeting Web site owners serving banner ads through Google’s AdSense program. In this scam, the fraudsters demand bitcoin in exchange for a promise not to flood the publisher’s ads with so much bot and junk traffic that Google’s automated anti-fraud systems suspend the user’s AdSense account for suspicious traffic.































Let's personalize your content