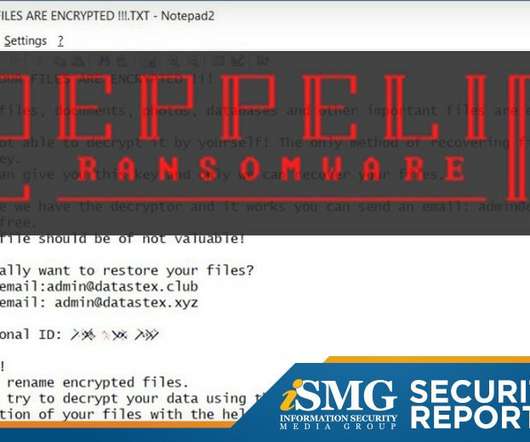
Ransomware Group Zepplin Punctured by Cybercrime Karma
Data Breach Today
NOVEMBER 24, 2022
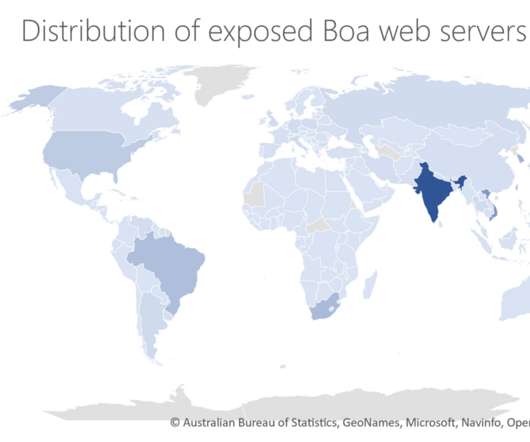
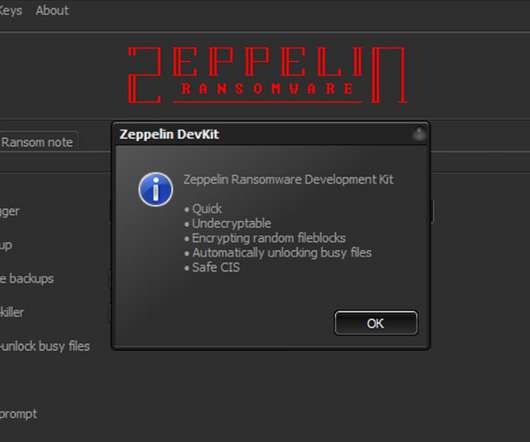
The latest edition of the ISMG Security Report discusses how the profits of ransomware group, Zepplin, have been smashed by security researchers, the risks of trading cryptocurrencies, and vendor Extrahop's newly appointed, high-profile president.















Let's personalize your content