New RAT Targets Russian Speakers
Data Breach Today
AUGUST 3, 2021
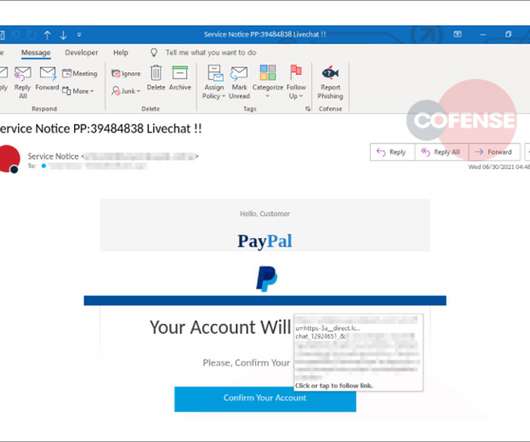
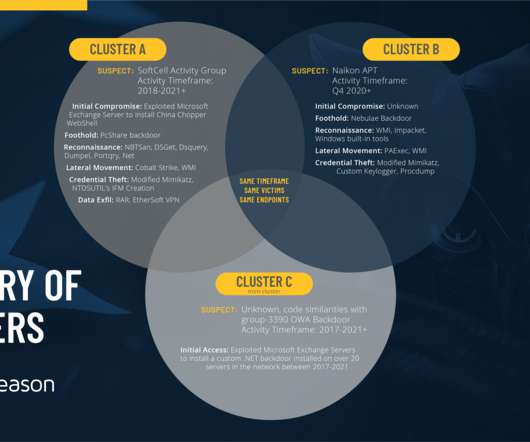
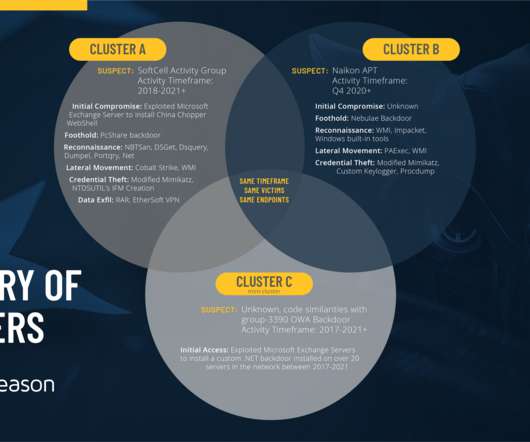
Malwarebytes Describes Unusual Tactics The Malwarebytes threat intelligence team has discovered a remote access Trojan apparently designed to target Russian speakers that may have combined a social engineering technique with a known exploit to maximize chances of infecting targets.


































Let's personalize your content