SolarWinds Attack: 'This Hit the Security Community Hard'
Data Breach Today
DECEMBER 29, 2020
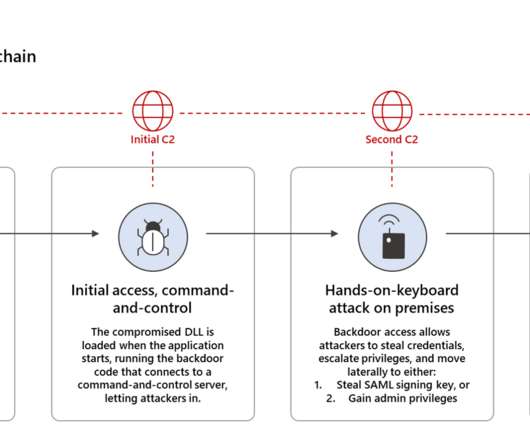
RiskIQ CEO Lou Manousos Details Lessons to Learn in Supply-Chain Attack Aftermath The SolarWinds breach is a case study in how attackers can subvert a widely used piece of software to turn it to their advantage, says Lou Manousos, CEO of RiskIQ. The attack surface management expert details lessons all organizations must learn in the wake of this "unprecedented" attack.








































Let's personalize your content