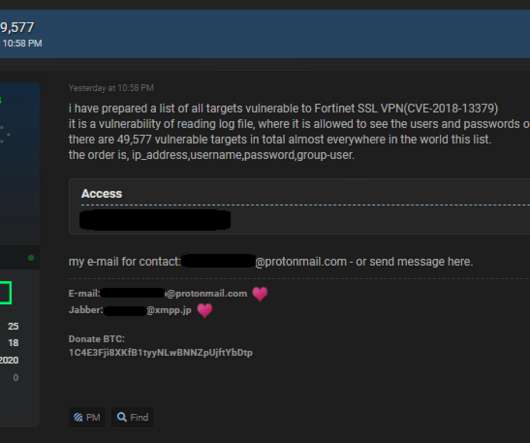
Threat actor shared a list of 49,577 IPs vulnerable Fortinet VPNs
Security Affairs
NOVEMBER 22, 2020
A threat actor has published online a list of one-line exploits to steal VPN credentials from over 49,000 vulnerable Fortinet VPNs. A threat actor, who goes online with the moniker “pumpedkicks,” has leaked online a list of exploits that could be exploited to steal VPN credentials from almost 50,000 Fortinet VPN devices. Researchers from Bank Security first reported the availability of the list of 49,577 IPs vulnerable to Fortinet SSL VPN CVE-2018-13379.















Let's personalize your content