Supercomputer Intrusions Trace to Cryptocurrency Miners
Data Breach Today
MAY 18, 2020
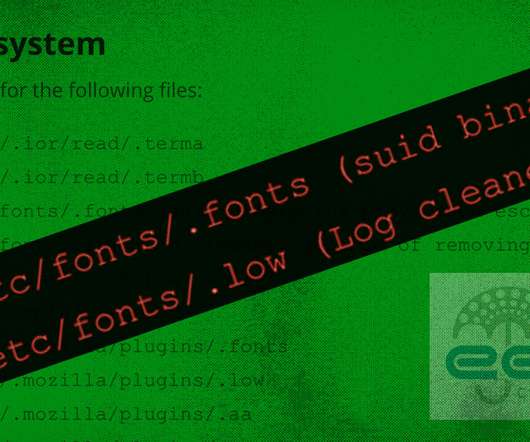
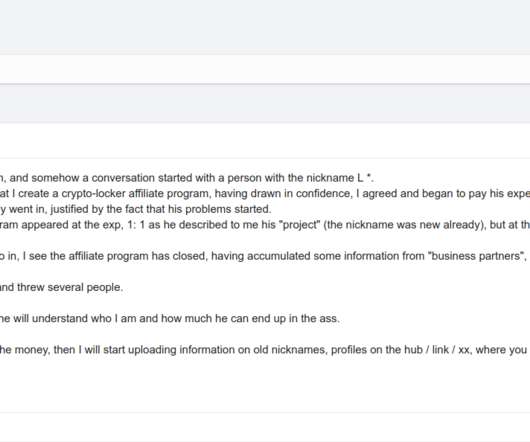
Likely Connected: Attacks Against Systems in US, UK, China, Germany and Beyond Cryptocurrency-mining hackers appear to be behind a recent spate of supercomputer and high-performance computing system intrusions. But it's unclear if attackers might also have had data-stealing or espionage intentions.





































Let's personalize your content