Thunderbolt Flaws Expose Millions of PCs to Hands-On Hacking
WIRED Threat Level
MAY 10, 2020
The so-called Thunderspy attack takes less than five minutes to pull off with physical access to a device, and affects any PC manufactured before 2019.

WIRED Threat Level
MAY 10, 2020
The so-called Thunderspy attack takes less than five minutes to pull off with physical access to a device, and affects any PC manufactured before 2019.

Security Affairs
MAY 10, 2020
Stadler, a Swiss manufacturer of railway rolling stock disclosed a data breach, hackers attempted to blackmail the company. International rail vehicle manufacturer, Stadler , disclosed a security breach that might have also allowed the attackers to steal company data. Attackers confirmed that attackers compromised the IT network of the company and deployed some of its machines with malware that was used to exfiltrate data from the infected devices. “Stadler internal surveillance services f
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
MAY 10, 2020
Pick who sees your tweets, posts, and stories—and choose what you want to see, too.
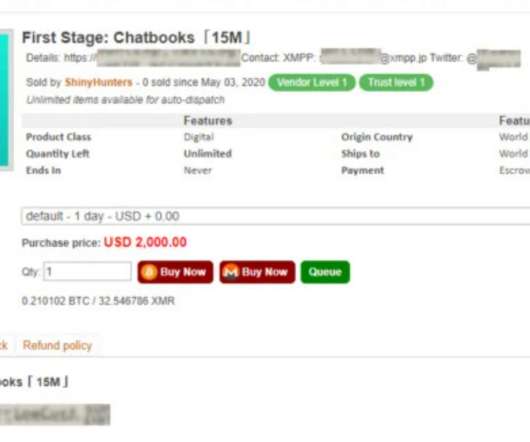
Security Affairs
MAY 10, 2020
Shiny Hunters hacking group is offering for sale on a dark web marketplace databases containing over 73.2 million user records from over 11 companies. A hacking group named Shiny Hunters is attempting to sell on a dark web hacking marketplace databases containing more than 73.2 million user records from 11 different companies. Shiny Hunters started offering the Tokopedia dump last week (90 million user records), then it began proposing 22 million user records for Unacademy and data allegedly obt

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Information Governance Perspectives
MAY 10, 2020
In May of 2020 I was honored to speak at the MERv conference with John Frost of Box on the topic of Using Information Governance with a Privacy Compliance Plan as the Fulcrum for Data Privacy and Continuous Compliance. Below are some excerpts from my transcribed remarks. Session Description: Tackling data privacy and maintaining consumer trust… Read More » Using Information Governance with a Privacy Compliance Plan as the Fulcrum for Data Privacy and Continuous Compliance The post Usi
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Information Governance Perspectives
MAY 10, 2020
In May of 2020 I was honored to speak at the MERv conference with John Frost of Box on the topic of Using Information Governance with a Privacy Compliance Plan as the Fulcrum for Data Privacy and Continuous Compliance. Below are some excerpts from my transcribed remarks. Session Description: Tackling data privacy and maintaining consumer trust is harder than ever, especially with the sheer amount of information you need to manage and with constantly evolving privacy laws (CCPA, GDPR, etc) movin
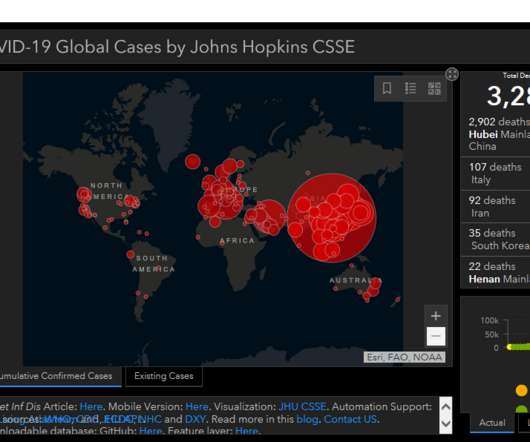
Security Affairs
MAY 10, 2020
This post includes the details of the Coronavirus-themed attacks launched from May 03 to May 09, 2020. Threat actors exploit the interest in the Coronavirus outbreak while infections increase worldwide, experts are observing new campaigns on a daily bases. Please give me your vote for European Cybersecurity Blogger Awards – VOTE FOR YOUR WINNERS [link].

Information Governance Perspectives
MAY 10, 2020
In May of 2020 I was honored to speak at the MERv conference with John Frost of Box on the topic of Using Information Governance with a Privacy Compliance Plan as the Fulcrum for Data Privacy and Continuous Compliance. Below are some excerpts from my transcribed remarks. Session Description: Tackling data privacy and maintaining consumer trust Continue reading.

Security Affairs
MAY 10, 2020
A new round of the weekly newsletter arrived! The best news of the week with Security Affairs. Please give me your vote for European Cybersecurity Blogger Awards – VOTE FOR YOUR WINNERS [link]. Coronavirus-themed attacks April 26 – May 02, 2020 Cyber Threats Observatory Gets Improvements Indias Jio Coronavirus symptom checker exposed test results TOKOPEDIA e-commerce hacked, 91 Million accounts available on the darkweb DHS CISA alert provides recommendations on securing Office 365 installs Hacke

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Let's personalize your content