Fake Labor Department Emails Designed to Spread TrickBot
Data Breach Today
MAY 4, 2020
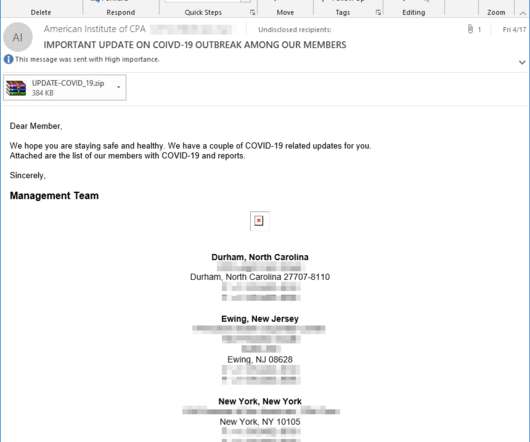
IBM: Spam Leverages Interest in Family and Medical Leave Act In an apparent attempt to spread TrickBot malware, cybercriminals are sending fake emails designed to look like notifications from the Labor Department concerning changes to the Family and Medical Leave Act, according to IBM X-Force.








































Let's personalize your content