Sued by Meta, Freenom Halts Domain Registrations
Krebs on Security
MARCH 7, 2023
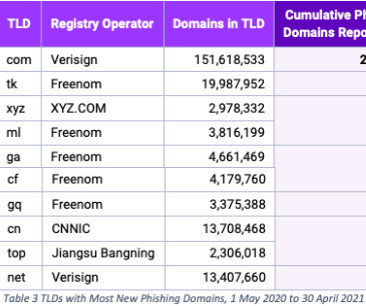
The domain name registrar Freenom , whose free domain names have long been a draw for spammers and phishers, has stopped allowing new domain name registrations. The move comes just days after the Dutch registrar was sued by Meta , which alleges the company ignores abuse complaints about phishing websites while monetizing traffic to those abusive domains.







































Let's personalize your content