How to implant a malware in hidden area of SSDs with Flex Capacity feature
Security Affairs
DECEMBER 31, 2021
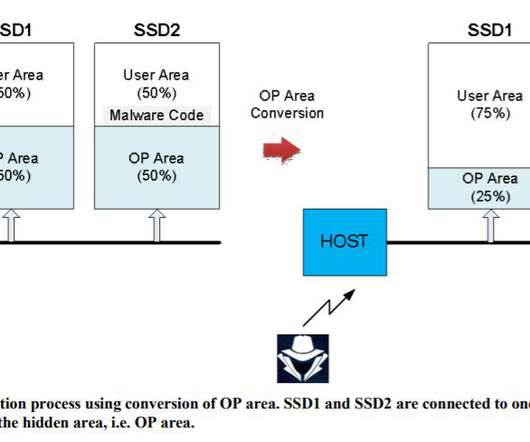
Researchers devised a series of attacks against SSDs that could allow to implant malware in a location that is not monitored by security solutions. Korean researchers devised a series of attacks against solid-state drives (SSDs) that could allow to implant malware in specific memory locations bypassing security solutions. The attacks work against drives with flex capacity features and allow to implant a malicious code in a hidden area of SSDs called over-provisioning.
















Let's personalize your content